Do you know what is the most predictable trend in Information Risk Management ?
It is vulnerabilities. If you review data breach reports from the last few years, you will notice one thing that is very consistent and it is about the vulnerabilities! The only change is that things have become worse over the years, and looks like the trend will continue.
Does it say something about our approach to managing vulnerabilities? Perhaps!
So are we missing something? Perhaps!
In this post I have pulled out 5 trends that I feel clearly indicates that the current approach of vulnerability management is not working, and it is time to re-think our approach.
#1 Software is (highly) vulnerable
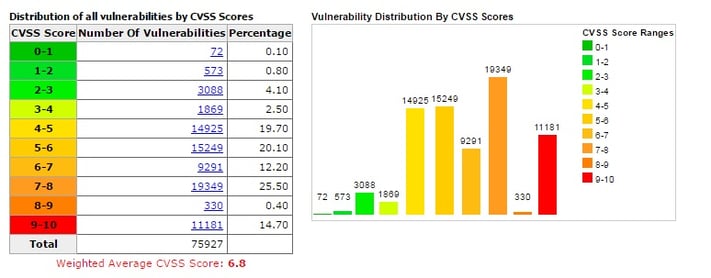
(Source: CVSS distribution, CVEdetails.com May 2016)
As of today there are 75,363 vulnerabilities, out of which 2,549 were added in 2016 so far. Given the exciting times of new technologies like IoT, Blockchain, Cloud, etc this trend is only going to change for the worse.
The bigger concern is that there are 11,181 vulnerabilities that fall into the 9-10 category - the highest score for severity as per CVSS. And this is not a manageable number by any means. Also the CVSS table is heavily tilted towards the right with a strong hue of red, as is visible above.
So if you go by the CVSS scores - everything is important unless stated otherwise!
#2 Exploiters are quick(er)
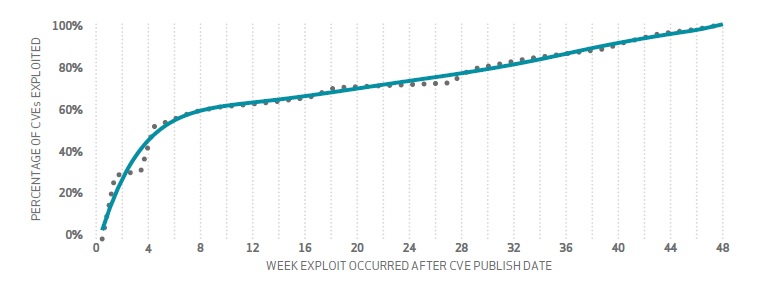
(Source: Cumulative % of CVEs exploited vs. CVE publish date. DBIR 2015 )
You can see that the majority of vulnerabilities i.e more than 50% of them got exploited within 4 weeks of the CVE publish date. Also, if it has a fancy name (and logo) like Heartbleed, Badlock, etc it might be even quicker because the bad guys will pay more attention - just like you and me.
So the time window to remediate is short, and getting shorter. Are your scan cycles actually putting you in a blind spot?
#3 We are fighting fires (every day)
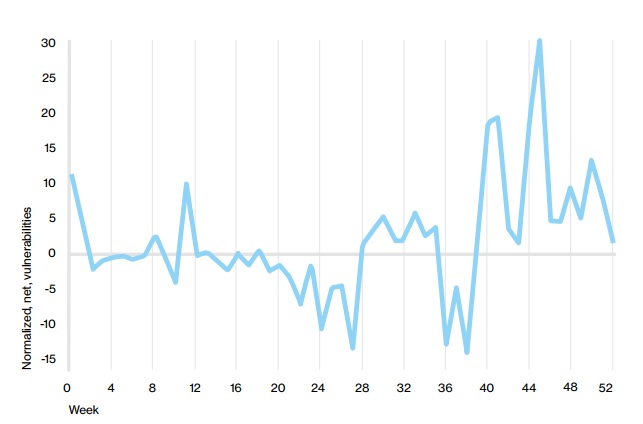
(Source: Delta of number of vulnerabilities opened each week and number closed. DBIR 2016)
During most weeks - The number of vulnerabilities opened is higher than the number closed. Which simply means that on any given day there is more in your IN box compared to the ones in your OUT box. Which by the way also means there are many people looking to talk to you. Not a good sign from an operations perspective.
So it is bad that you are continuously in a catch-up mode. And probably have no time for other luxuries in life like bio breaks and strategies beyond day-day fire-fighting!
#4 Old vulnerabilities continue to haunt
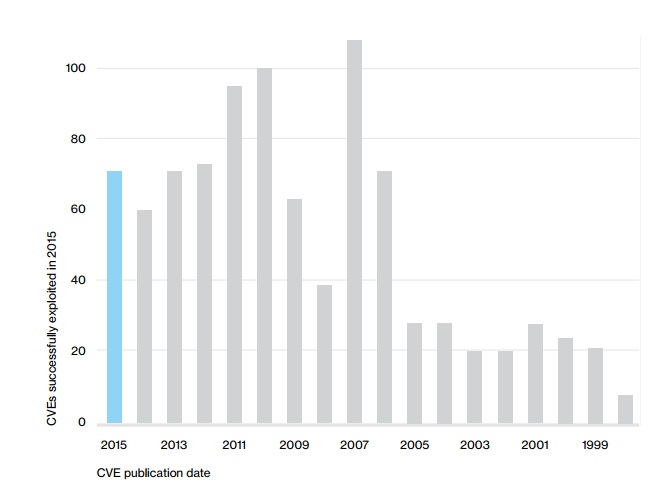
(Source: Count of CVEs exploited in 2015 by CVE publication date. DBIR 2016)
The above data indicates that - it doesn't really matter when the CVE was published, old vulnerabilities are still getting exploited in large numbers today. Old hits from the 90's are still popular today. Maybe it is true that exploiters use some kind of data and strategy to do their job? They definitely know your soft spots!
So you need a way to keep track of every piece of old junkie in the attic. You might have forgotten about them, but there are people watching!
#5 Patching is looking that (other) way
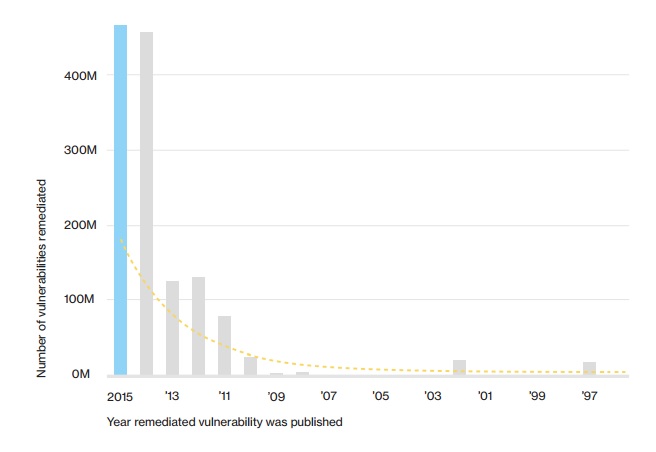
(Source: Closure rate of CVEs by CVE publication date. DBIR 2016)
Look at this interesting chart above. The vulnerabilities remedied in 2015 were more concentrated on the CVEs published in the same year or a couple of years before. Looks like a good job right? Wrong. If you look at the earlier chart in #4 - you see how disconnected they are. If older vulnerabilities are getting exploited, why is all the effort concentrated on the newer ones? You definitely need a better way to know which ones are important to the exploiter!
So knowing the right assets to patch is much more valuable than sprinting to patch for the latest and greatest vulnerabilities.
CONCLUSION:
If I have to summarize the above 5 facts in 2 sentences -
You need a better way to know which vulnerabilities are critical, and you should have a water-tight process to remediate (or mitigate) them as quickly as possible.
Remember vulnerabilities are here to stay, CVSS scores are not that helpful, and the exploiters do not wait (usually). And you are busy !
One way of doing this is by using our Security Analytics and Visualization Platform (SAVP) which helps to make your Vulnerability Management Program more effective and efficient by using Analytics along with Intelligence.





