There can be no argument that vulnerability management is one of the oldest challenges in cybersecurity. There are many reasons why it has remained a problem, even today.
Let's understand vulnerability intelligence and the challenges it is trying to address. Vulnerability intelligence is not the same as threat intelligence.
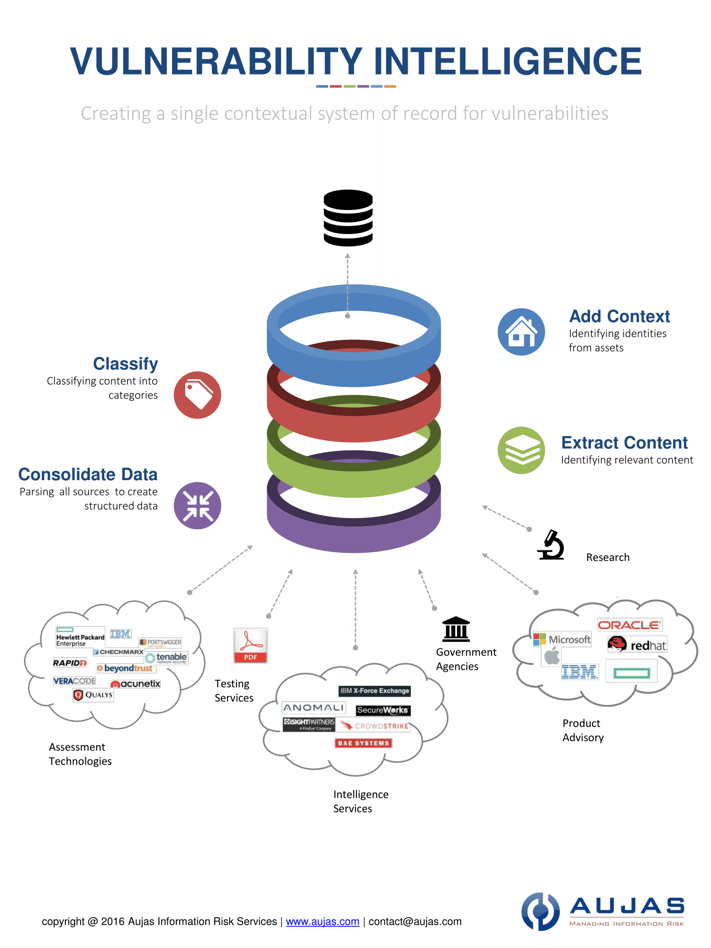
Vulnerability Management is about data. The data challenges related to vulnerability management is explained in this infographic:
Vulnerabilities can be mitigated by consolidating large sets of data, irrespective of the sources, formats, structured/unstructured, offline/online, and isolating those that matter the most to your organization.
Vulnerability Intelligence enables creating a record system for vulnerabilities by consolidating available sources, external and internal, including your assets and offline CMDB.
It consolidates data based on context enabling analytics tools to derive insights on how to mitigate risks.
Here is how it works.
To know more about vulnerability management, get in touch with Aujas security experts at contact@aujas.com.






