What is common between "Hacking the Pentagon" and "Hacking Google CEO's Quora account"?
It is Bug Bounties ! The former was a super successful bounty program run by the US government last month. The latter is a hacking incident this week, "in-spite" of Quora having a bounty program.
So the million $ security question - If you are an enterprise CISO, should you go for a bug bounty program?

(Image credits: eset.co.uk)
What is a Bug Bounty Program?
In simple terms, It is a way to encourage responsible disclosure from the larger security research or hacker community. Responsible disclosure means alerting the company about the vulnerability in the software, and providing them an opportunity to fix it first.
Why would anyone do that?
Unlike the bad world of cyber criminals, the research community or good hackers, hack into a system for the kick of it and it is a good cyber-citizen behavior for them to act responsibly and not cause harm to the parties involved.
Many companies have a Responsible Disclosure program for security vulnerabilities.
Some of them like Facebook, Google, Microsoft, AT&T, etc. have a Reward in the form of money (and of-course fame comes with it).
Some others like Apple, Adobe, Oracle, Netflix, Amazon Retail, etc just provide fame in the form of Hall of Fame.
Others like AWS, Cisco, EMC, Box, LinkedIn, etc just have a way to report vulnerabilities, without money or fame.
Each have their own pros/cons. Bug Bounty as the name suggests is the one with Money.
Why should you go for it? (What are the benefits)
There is no doubt that running a bounty program would get you the best talent for "pentesting" your security. This is especially important given that there is a crunch of talent in the info sec industry.
(to know more about talent crunch checkout this article - 10 Ways CIOs & CISOs Can Beat Talent Crunch in Information Security ).
Bounties will help you to unearth vulnerabilities, that you might not be able to find in similar time frames if you rely only on your own limited resources. The value of the crowd is immense in this case.
Also unlike what it sounds, bounties are not about unlocking the gates of your kingdom for bad people to go wild.
There is a method to the madness and it is a "contained" exercise. Or at-least that is the intention.
You typically open it up for some areas of your infrastructure, and you also vet the participants before hand. Also you have a plan to remediate within a short time frame, so that the vulnerabilities discovered are patched/mitigated before it gets out of hand (to the wrong hands of-course).
There have been cases in the past where things have gone wrong, but net-net it has been positive for most people.
If you are not a large enterprise like Google or Facebook (read: companies with the right resources) - you can still host a bounty program. There are platforms/cloud services that helps you to manage the program end-end. You pay them a commission (typically ~20% of the bounty), and they take care of everything.
Examples HackerOne, BugCrowd, CrowdCurity, Synack, Etc.
You can also have private programs with by-invitation-only pre-vetted researchers/hackers participate. Which makes sense if yours is a critical infrastructure.
One of the key challenges in any bounty program is the Duplicates - those entries who find the vulnerability, yet do not qualify for the prize because someone else submitted it before them. This is one of the top reasons for disgruntlement, hence has the risk of the researcher/hacker going rogue. These platforms have points system that helps reward duplicates in other ways, thus reducing the risk of a disgruntled hacker.
As expected these bounty programs have been popular with technology product companies. But now it is finding new patrons in other industries, including IT, Banking and Entertainment as you can see below.
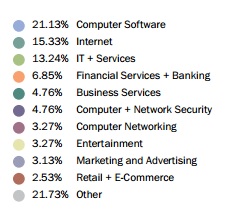
(source: State of bug bounty 2016, BugCrowd)
Government is the new entrant. After the success of "Hack the Pentagon" by the US, Governments across the world, including Russia are thinking of having bounties.
In my opinion - A bounty program definitely helps manage responsible disclosures better since the efforts/rewards are balanced, and outsourcing it to companies who might have more expertise in managing such programs makes a lot of sense from a planning & execution perspective.
It is definitely better than asking people to make submissions at security@xyz.com email address.
What are the challenges? (What is in the "fine print")
Bounties are good. So what is the problem?
Well. Having (or not having) a bounty program does not guarantee a secure organization!
Example: This week a group called OurMine hacked into the Quora account of Google CEO Sundar Pichai, (and posted messages to his 5M followers via the connected social accounts.) They said they gained access to his account using security vulnerabilities that they had earlier reported to Quora. Incidentally, Quora has a bounty program hosted on BugCrowd.
Discovering critical security vulnerabilities is a step in the right direction.
But having said that - It is one of the very first steps. Remediation is an important next step. Also what your bounty program covers might be just a small % of your overall IT/Data infrastructure and it is critical to remediate all the "right" vulnerabilities keeping the larger organization context in mind.
In addition, vulnerability management is cyclical - vulnerabilities are a moving window and they constantly change as the days pass by. On an avg 18 new vulnerabilities are added every day.
There are many challenges with vulnerability management for an enterprise.
(to know more about challenges in vulnerability management programs checkout this article - CISOs - 10 Questions to Find if Vulnerability Management is Working )
CONCLUSION:
Bug Bounties are a smarter way to manage your Responsible Disclosures' Program for Security Vulnerabilities. But do remind yourselves that it is one piece of the larger jigsaw puzzle called Information Security.
It will work if and only-if you have a rock solid information security management strategy and execution capability in place.
@Aujas, We can help you in 3 ways as follows:
1. Help Manage Information Risk Comprehensively with our Practice Expertise across Risk Advisory, Identity/Access Management, Threat/Vulnerability Management, Security Intelligence & Operations, and Digital Business Security, where we can help strategize, plan, implement and maintain your security programs with our best-of-breed consultants across the globe.
2. Help Provide the "State of Security" View with our Security Analytics & Visualization Platform (SAVP) that can be customized to your specific use-cases like Vulnerability Remediation, Client Assurance, Third Party Assurance, Product Security, Product Enhancement (Qradar SIEM), Data Leakage, etc.
3. Help Enhance your Security Programs with our Platform-as-a-Service Offerings like Co-managed security, Vulnerability intelligence, Vendor Risk management, Data protection, etc by retaining your existing tools and investments, but filling the missing gaps with our platform/services, and do it with an overall cost savings to you.
To know more, talk to our security experts by clicking here






