Single Sign-On (SSO) is a user authentication service that allows a user to access various systems using one set of login credentials within any organization. SSO creates a single point of authentication, allowing users to create and use a unique identity across digital properties associated with an organization.
SSO is a buzzword in the IT industry for a while now, and why shouldn’t it be? SSO was born due to the exponential growth of applications, and it becomes a big task to keep track of different passwords users use to access various applications. On the other hand, using the same password for multiple apps is a bad practice; a single application database hack can lead to unauthorized access to many other applications. This is where Single Sign-On comes to play.
SSO Simplified
Let us say, you need to enter a party in a club without personal invitation, but you know a friend well known in the place that can vouch for you and tell the guy at the entrance to let you in.
Let’s enact this situation through the following metaphors:
- You, the visitor (user agent/favorite browser)
- A Club (a service/web application you want to access)
- Your friend (a well-known trusted service that provides the Single Sign-On option (e.g., Google))
- The guy at the entrance (login page of the service/web application)
Now, you want to get into the club and decide to go directly to the tough guy at the entrance. He looks at you and asks for an invitation. Instead of taking out your invitation, you tell him that you know Barney, and he can confirm that you are a worthy person to be allowed inside.
Looking at you frowningly, the guy at the entrance gets his phone and dials Barney, “Hey, Barney. What’s up, man? It’s me, the guy at the entrance. I have got a dude here that claims you know him and can vouch for him. Yeah, sure.”.
Then he gives you the phone and, you greet Barney, “Hey! It’s me, yeah how are you bro, I am at the club entrance and can you please tell this big guy...”. After Barney recognizes you, the phone is returned to the guy at the entrance. The guy listens to Barney for a while, then looks at you with a smile and lets you into the club smirking.
So, this guy at the entrance let you in even without an invitation, seeing you for the first time in his life! And this is just because both of you know Barney very well. The most awesome part is that almost all guys at the entrance of nearly all nightclubs know Barney!
Here is the same situation for accessing a web service or application. You open the login page of the service you want to use. Without entering any credentials, you click the “Sign in with Google” button.

The service redirects you to the Google login page. You specify your login and password or just approve by sending your identification data to the third-party service if you already logged in via Google in this browser session. Google sends a direct request to the service telling who you are. The service gets this information and then returns to you with a new page, allowing the access.
Now let’s understand above enacted situation using a simple diagram:
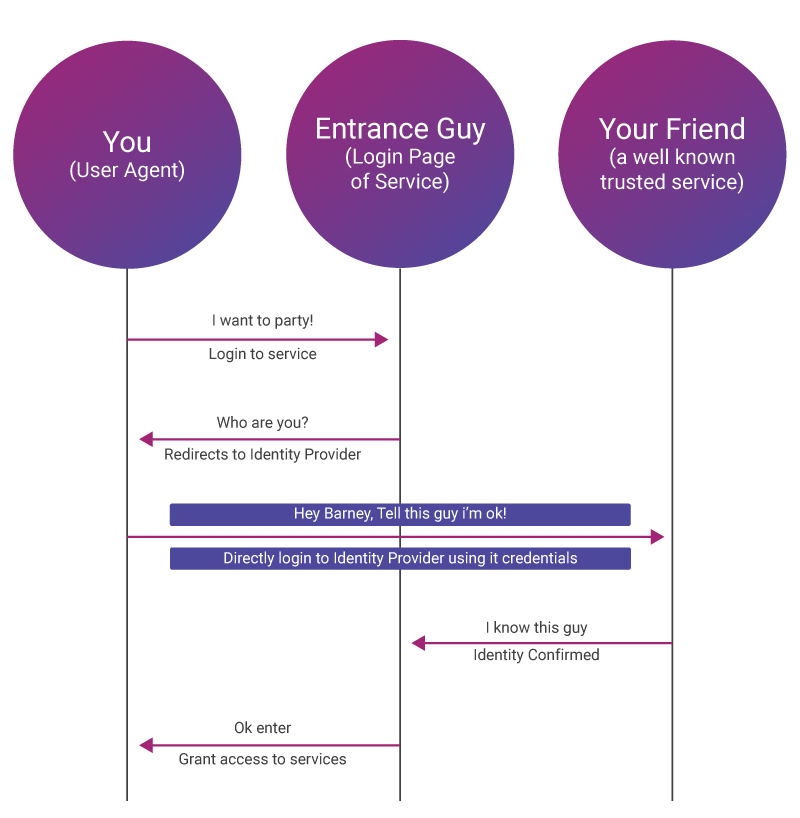
So, now we have seen that the Single Sign-On makes authentication on multiple systems more convenient and secure. The fact that a person does not have to remember multiple passwords for different systems or take a risk using the same password everywhere makes SSO a safe option.
To significantly increase security, we also have Multi-Factor Authentication (MFA).
Besides a password, it includes another authentication step:
- Something you know (answer to a security question)
- Something you are (biometrics including retinal scan, voice recognition, etc)
- Something you have (a security token, One-time password (OTP), missed call on the registered number, etc.)
- Time
- Location
Questions an organization should be asking at this point
- Do I need to protect my organization’s network from unauthorized access?
- Are the organization’s users connecting from multiple remote locations?
- Does the business want fewer complaints or trouble about passwords for IT helpdesks?
- Do users need to access many password-protected applications?
- Do organizations want users to have a streamlined process of signing-in and using the application?
If you have answered “YES” for the above questions, Aujas can help you.
How Aujas can help you
Aujas Cloud Single Sign-on Quickstart offerings can avoid frequent user authentications by enabling a single set of login credentials. Aujas Cloud SSO and dual-factor authentication services give an organization ready-to-use templates, models, and application configurations with leading Cloud SSO SaaS solutions.
Aujas also devise the solution architecture and application integration models, along with reports and dashboards to meet auditory requirements. Organizations can also use Aujas’ services to add dual-factor authentication for their existing business applications.
Aujas has comprehensive expertise and experience in executing end-to-end SSO projects. With the proven ability to integrate even toughest apps with SSO solutions, Aujas leverages a pool of experts to successfully deal with a wide range of integration with dual-factor authentication.
Aujas SSO advantages include:
- Avoid unwanted permissions and ensure accurate entitlement.
- Manage user credentials to scale based on the proliferation of the solution used.
- Automated credential management to reduce manual interventions.
- Increased security through two-factor authentication.
To know more about Aujas SSO services, visit us here. or write to us at contact@aujas.com.




