Security vulnerabilities in applications are a nightmare. Mishaps and failures must be avoided during application development, testing, and deployment phases to mitigate the risk of a high-profile data breach. Application security must not be an afterthought and should never be compromised for functionality and speed. By identifying vulnerabilities in applications, networks, and infrastructure early in the development cycle, DevSecOps ensures that most of the vulnerabilities in the application are identified before the code is deployed for production.
DevSecOps leverage the workflow automation of DevOps for application testing, from code release to production. DevSecOps gives equal importance to security and functional testing to ensure consistency and efficiency. The implementation steps include introducing security across the end-to-end development lifecycle, ensuring development and operations teams take the shared responsibility of security and driving automated security checks at every delivery stage by embedding controls, tools, and processes in DevOps workflow.
The cloud security alliance has published a paper on the six pillars of DevSecOps. It clearly describes why an organization should embrace DevSecOps.
Collective Responsibility: The biggest challenge is to change the organization’s mindset to include security in DevOps. Security is every individual’s responsibility, and their contribution is critical to establishing awareness across the organization. Developers and users must be the first line of defense.
Collaboration and Integration: Collaborate to reduce the gaps in knowledge, talent, and resources for implementing a security culture. More security awareness through collaboration between functional teams helps prompt reporting of anomalies and avoidance of security incidents due to human error.
Pragmatic Implementation: Every software development cycle is different, be it process, tools, technologies, or maturity. The tools and technologies cannot be the same, and teams purchase more of these which are not seamless to deploy and operate, aggravating security risks. A holistic view of security is required while choosing the right platforms and solutions to ensure integrability and mitigate risks.
Bridging Compliance and Development: It is tough to convey compliance needs and translate them to a DevOps requirement. Even if the technical controls are implemented, it is not easy to get tangible proof that the security needs have been met. There is also a misalignment between agile development and compliance requirements due to the continuous evolution of software development models and practices. Proof is a must to convince regulatory authorities that there is a process to ensure audit of every process. The ideal way to bridge this gap between compliance and development is to recognize applicable controls, translate them to relevant software measures, and identify specific areas in the software lifecycle to automate these controls and measure their impact to enhance the quality of risk mitigation and ensure compliance.
Automation: Automation is a must for the security of a software build as it increases efficiencies, saves time, reduces manual workloads with a regular schedule of quality checks. Automated quality and security checks can ensure thorough, timely, and consistent feedback. It can help overcome the challenges of manual coding, testing, deployment, and patching that can lead to insecure software. Though automated security checks can lead to build delays or failures, these can be addressed through workflow improvements or semi-automated approaches.
Measure, Monitor, Report, and Action: Actionable metrics are the key to the success of DevSecOps as they help measure the progress and detect failures in the implementation and maintenance. A few essential metrics include frequency of deployment, vulnerability patch time, automatically tested code percentage, and the number of automated tests per application. The outcomes during software development and after delivery are continuously measured, monitored, and reported to ensure the success of DevSecOps.
Challenges in Implementing DevSecOps
The benefits of DevOps, such as better collaboration, faster time to market, increased efficiencies, improved security, etc., can be lost without the proper implementation of DevSecOps. A 2020 GitLab survey and Portswigger stats revealed the following issues and challenges in adopting DevSecOps.
Shift Left: In the pursuit to deliver better applications, the CI/CD pipelines see a rapid frequency and variety of deployments, leading to new vulnerabilities in applications. Though security professionals claim they are shifting security left, they are not able to scan for new vulnerabilities and weaknesses due to changing application versions and infrastructure components at various development lifecycle stages.
Adoption is yet to mature: DevSecOps is still a new practice; it’s yet to evolve as only 30% of security professionals claim they practice its implementation. Around 47% of the organizations have begun the process. Cybersecurity and development teams of most companies are still working in silos, and most firms are still considering converging people processes and technologies.
Developers outnumber security professionals: The GitLab report says the current trend is 500:1 developer to security professionals. This means organizations can benefit from automating more of their cybersecurity. By integrating security into development, you can leverage the power of those 500 engineers to help secure the software application development lifecycle.
Lack of security processes: Most security teams do not have automated processes and workflows for microservices/containers/APIs/cloud-native or serverless for continuous compliance checks, ensure integrity, and proactively address security risks.
Testing Traction: Over 42% of teams say testing happens too late in the lifecycle, 36% feel it was hard to understand, process, and fix any discovered vulnerabilities, and 31% say prioritizing vulnerability remediation is still an arduous task.
Access to security results: Developers are not getting immediate access to security results. If developers are to find and fix vulnerabilities, the scan results must be provided to their pipelines or native workflows. The other reason is that the number of vulnerabilities that find their way into production is so high that developers plan to deal with them later as they feel the vulnerabilities are of low priority or have other application fixes to deal with.
Let the shift begin
DevSecOps is changing the way companies approach security. Despite internal resistance in teams to move towards DevSecops due to various factors and misconceptions, the technological and business advantages are undoubtedly promising. The following are the steps you can utilize to transition to this methodology:
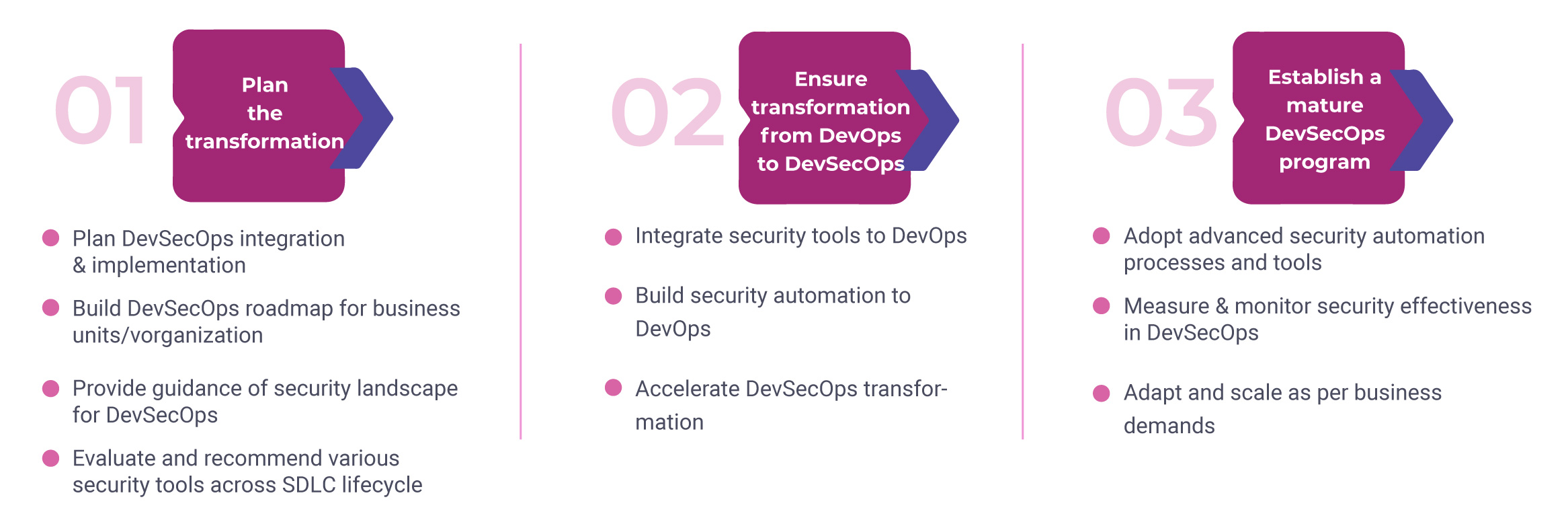
DevSecOps practices must be the core of DevOps. It strengthens product development cycles by avoiding common security snags and helps your organization sustain agility to mitigate any cyber threat. DevSecOps ensure easy remediation of vulnerabilities and is the ideal tool to minimize cost overruns. With the growing dependence on digital technologies, security is a must from the start as it can help developers quickly confront and fix security flaws to bring in a coherent approach to software delivery.
Eager to know more on how DevSecOps can ensure application security? Talk to our experts at contact@aujas.com





