Summary
MOVEit Transfer is a widely used file transfer automation software developed by Ipswitch, a US-based Progress Software Corporation subsidiary. Recent vulnerabilities within MOVEit Transfer allowed the Cl0p ransomware gang to exploit these loopholes and steal sensitive corporate information. While Progress Software released initial security patches, it still failed to remediate the issue. However, the most recent patch issued on July 6th, 2023, appears to have resolved the security flaws.
How to remediate the issue
If you use MOVEit Transfer, you need to install the following two vendor-issued patches to enhance your security:
- Security patch from May 2023: (found here)
- Service pack from July 2023: (found here)

Further security measures
The history of failed patches for this vulnerability raises concerns about future security, with questions being raised on if the July Service Pack will prove to be vulnerable in time. Organizations seeking additional layers of security can:
- Disable web traffic: If your business does not require MOVEit, you can mitigate the vulnerabilities by turning off HTTP and HTTPS traffic to the MOVEit servers. This approach will halt automation, but it would be a worthwhile tradeoff for certain businesses.
- Defend with managed detection and response (MDR): Aujas offers services in advanced detection and rapid response. Explore our solutions to learn how we can help your organization detect and defend against such ransomware attacks.
- Control access with identity and access management (IAM): Unauthorized user accounts pose a risk to MOVEit. Contact Aujas’ IAM team to control unwarranted and unnecessary privileged access to your systems.
Vulnerabilities full history
MOVEit is a popular automation software that encountered severe security vulnerabilities in May 2023 when the Cl0p ransomware gang began exploiting a SQL Injection vulnerability in MOVEit Transfer. This was further exacerbated because thousands of customers have MOVEit Transfer installed on servers connected to the open internet instead of installing it on servers protected behind a VPN.
The Cl0p gang stole sensitive information from various organizations, including world governments, big accounting firms, and prominent news organizations. They then demanded ransoms from the victims by threatening to release their confidential data publicly.
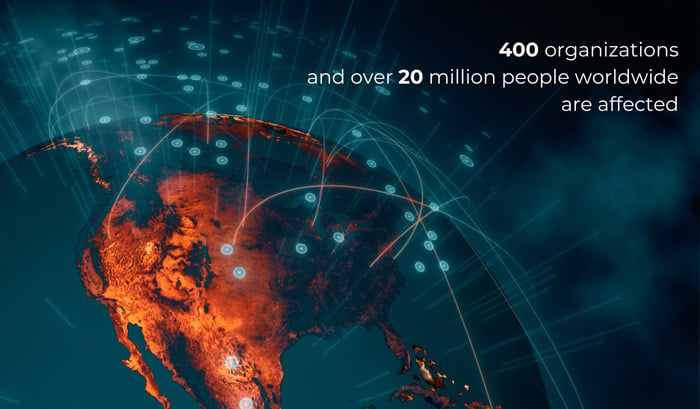
Progress Software, MOVEit’s maintainer, attempted to resolve the issue by releasing a security patch in May. However, the solution was inadequate, leading to major disruptions and data theft. MOVEit may go down in history as the biggest vulnerability of 2023, as it affected more than 400 organizations and over 20 million people worldwide.
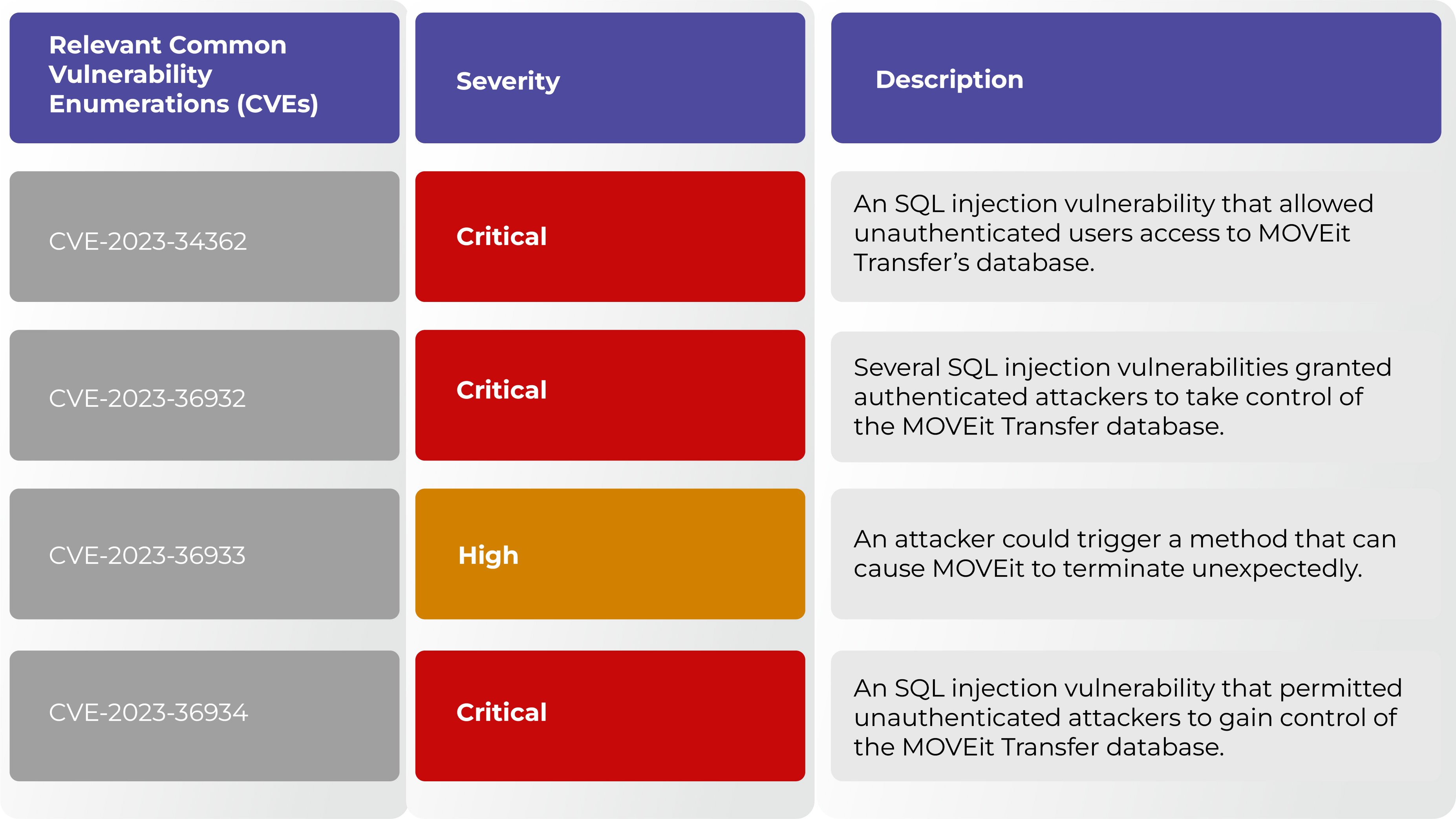
Detailed overview of MOVEit vulnerabilities
The details of the numerous vulnerabilities in MOVEit Transfer are outlined in the below CVE table.
The Aujas difference
We are a strong team of more than 1,000 cybersecurity professionals working together to keep our clients safe. Our high-quality services have earned us a remarkable 95% customer retention rate, reflecting that we deliver great value at a reasonable cost.
Our service offerings include IAM, MDR, risk advisory, custom security solutions and more! Contact us today to explore how we can fortify your organization's security.






