As Information Technology (IT) evolves and industries undergo digital transformation, understanding the depth of Operational Technology (OT) becomes crucial. The need to operate with the interconnected system has increased for today's manufacturing sectors. The technological integration of IT & OT networks has transformed how industrial organizations function.
Operational technology integrates hardware and software with network connectivity to monitor and control industrial processes, devices, and infrastructure. It encompasses the device and technology that controls industrial assets and operations. To explore the security aspect of operational technology, let's learn what, why, and how of OT security.
What is OT Security?
OT security involves the application of cybersecurity software/service to monitor, analyze and control industrial processes and devices on-site and remotely. It facilitates centralized access to industrial hardware with a comprehensive view of the entire operational infrastructure.
With OT security implementation, IT security teams can manage the operational technology from end to end and mitigate risks to prevent cyber-attacks. In addition, it helps to protect the information, IT assets, & people and perform changes to enterprise OT systems.
The OT cyber security solutions are designed to secure industrial systems and networks. It deals with increasing cyber criminals targeting machine-to-machine communications, embedded systems, and other assets. Today's OT security involves next-generation firewalls (NGFWs), security information and event management (SIEM), identity access and management(IAM), and more.
Why OT Security?
Traditionally, OT systems were distinct and disconnected from the internet. Thus, cybersecurity efforts were compromised due to a lack of transparency. Additionally, identifying the boundaries of the attack surface was tricky, which increased the possibility of being exposed to cyber threats.
Cybercriminals can discover vulnerabilities in legacy systems and continue to exploit them effortlessly. Hackers find several ways to penetrate the operational infrastructure if organizations do not upgrade their operational technology.
With the Industrial Internet of Things (IIoT), the distinction between OT systems and the IT environment is blurring. The convergence of OT and IT networks gave rise to a complex network that requires sophisticated OT security solutions.
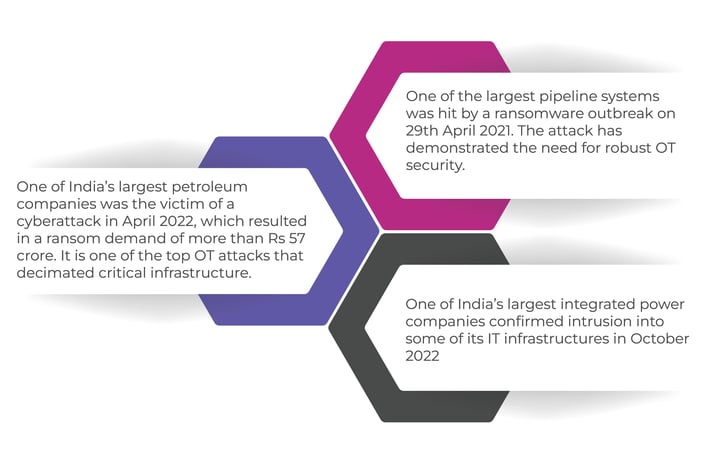
The recent real-time OT attacks illustrate the need for OT security in industries such as oil & gas, manufacturing, electrical generation and distribution, maritime, aviation, rail, and utilities, etc.,
How do Organizations implement OT Security?
Implementing cybersecurity programs for heterogenous and legacy OT environments demands more time and resources. In today's hyper-digitized industrial environment, organizations need a forward-looking security strategy. It helps to ensure that industrial transformations are uninterrupted with stable OT cybersecurity. Consequently, the OT security strategy should deliver emerging technical and procedural capabilities and ensure the continuity of industrial operation and organizational resilience.
Organizations seeking to implement OT security programs successfully will:

How Aujas Can Help You?
Aujas renders OT security services through OT & IT security capability model, offering the following:
-
Full visibility into assets using Passive and Active discovery techniques
-
Continuous monitoring for threats and vulnerabilities
-
Interoperability with SIEM, SOAR, and XDR to monitor and protect against attacks
-
Risk assessment through various OT security management platforms
-
Flexible deployment in on-premises, cloud, or hybrid.
To know more about OT security services, talk to our security experts at contact@aujas.com.





