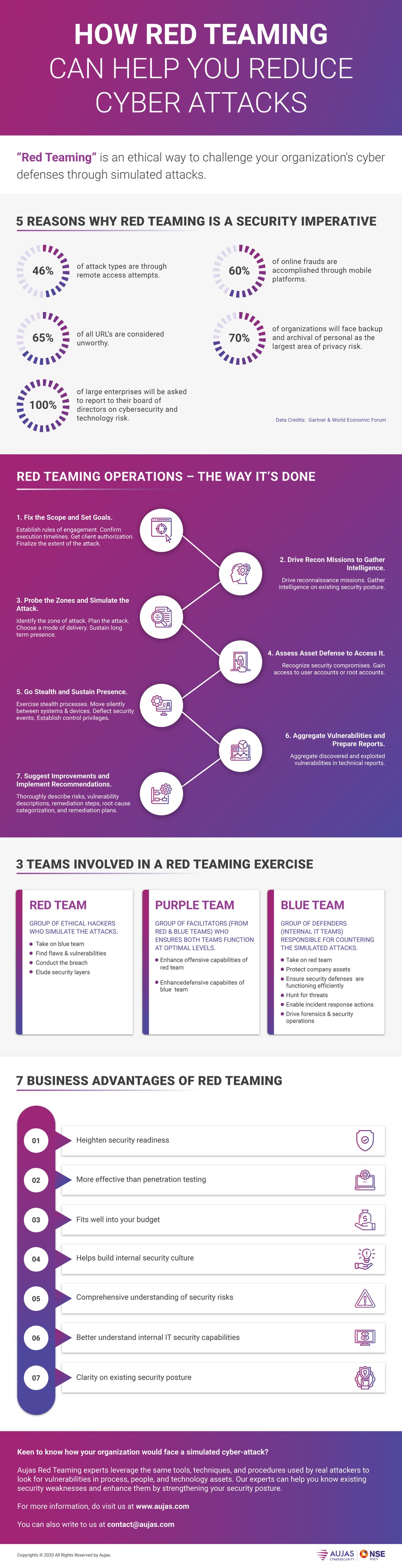
Sophisticated threats and attack vectors cannot be minimized by perimeter level security controls, firewalls, and antivirus programs. Such controls and programs can easily be breached, to reduce such risks, you need a phased approach to evaluate your security environment across physical and systems layers of the infrastructure.
By adopting a red teaming exercise, your IT teams can gain immense clarity into current security posture by knowing the type of vulnerabilities and threats facing the organization. The exercise can also help you increase awareness of security complacencies and focus on areas that need improvement and investment.