Phishing emails are rampant these days and are one of the sophisticated forms of cyber attack. These suspicious emails help fraudsters hack various enterprise assets and steal sensitive data. Phishing is a hacker’s favorite attack vector. Their objective is to trick users and make them believe they are dealing with trustworthy authority and get their data or system access. Phishing activities are on the rise; it is more important to face this reality and not be gullible or scammed as these are easier to spot.
Here is an impressive list of Phishing tactics you must be aware. Being aware of them can help you prevent a toxic trail of breaches.
- Deception Phishing
One of the most traditional approaches to Phishing is to send out a mass email and try to convince users to click the link in the message, such as the one shown below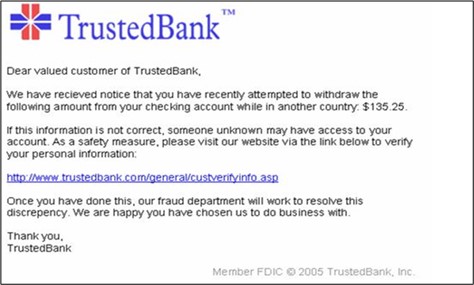
- Tab-Nabbing
Tab-nabbing techniques seek to impersonate popular websites that have been left unattended for some time and convince users to re-enter their credentials.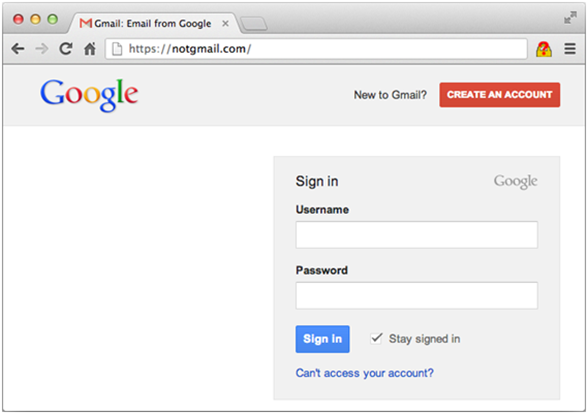
- Malware Based Phishing
Malware based Phishing, a strategy typically aimed at small and medium-sized businesses (SMBs) inserts malware onto a user’s computer (by email attachment, download, etc.) to gain information and exploit vulnerabilities. SMBs frequently have weak patch management policies, thus forgetting applications and operating systems updates – which often have patches to harden the system against these attacks.
Ransomware is a particular type of malware that is getting increasingly popular. It involves encrypting the victim’s data and asking for a ransom to decrypt it.
68% of 200 security professionals surveyed by TripWire during the 2016 RSA conference expressed concern that their company would not be able to recover from a Ransomware attack fully.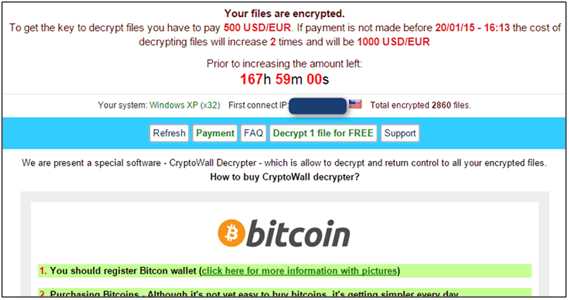
- Key Loggers and Screen Loggers
Key loggers and screen loggers are a type of malware that can record a user’s keystrokes and activities – sometimes even your entire display. Computers can become infected with key loggers and screen loggers when users visit individual web pages or complete downloads such as applications and device drivers. Phishers use this method to intercept any information input to the system once sent to the designated collection server.
Spyeye, one of the more popular keyloggers, plagued the financial services industry for years by quietly stealing customer account information by recording keystrokes.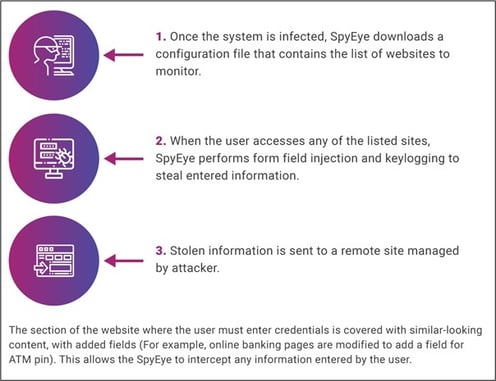
- Web Trojans
One of the most devious and deceitful phishing methods involves web Trojans, which are malicious programs used to collect a user’s login credentials while disguising itself as a specific website – e.g., a company login portal, a social media platform, or an email account. The user believes they are entering their ID and password into this website when they have just submitted their credentials to a phisher.
The Dyre Banking Trojan was delivered by emails disguised as JP Morgan & Chase advertisements. These trojans were able to pass through anti-virus software, allowing them to remain undetected for considerable periods.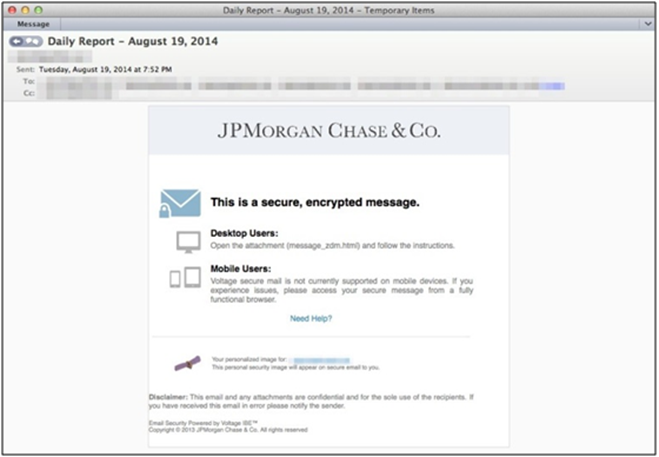
- Data Theft
By implanting malicious code on a user’s computer, phishers can steal confidential information. Not only is this tactic widely used to collect social security and bank account numbers, but this is known as an effective method for corporate espionage.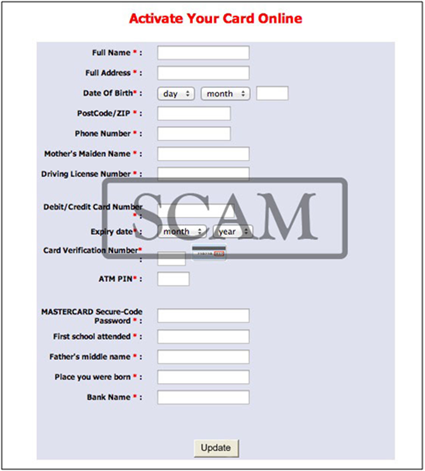
- Content Injection
When hackers gain access to the back-end of websites, they can often tweak content to be misleading, resulting in users submitting sensitive information.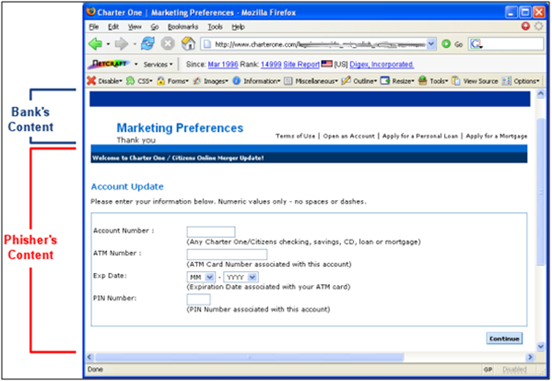
- System Reconfiguration Attacks
Hackers can modify system settings on user desktops to create holes in endpoint security that can be further exploited – such as updating URL favorites to redirect to malicious websites and even disabling endpoint anti-malware endpoint’s administrative privileges.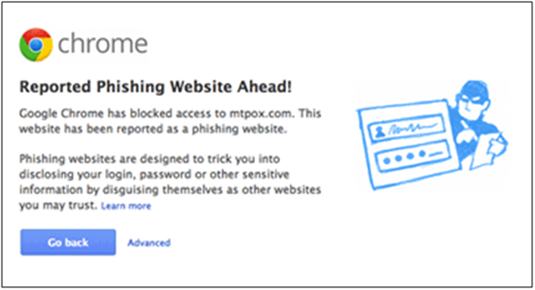
- Search Engine Phishing
Search engine phishing occurs when phishers create websites with “offers” – often too good to be accurate and have them indexed systematically within popular search engines.
Users stumble upon these sites in their usual searches and often fooled into providing information to receive the offer (which can be a false bank offering low-interest rates, insurance solutions, etc.)
- Man in the Middle (MitM)
Quite possibly the most challenging type of attack to detect, MitM phishing attacks occur when hackers position themselves between users and legitimate websites – resulting in the interception and recording of any data sent to the website.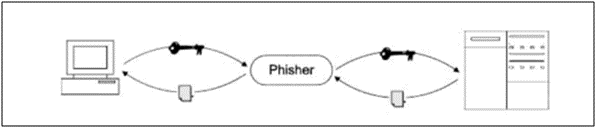
- Session Hijacking
Session hijacking occurs when malicious software “hijacks” a user-initiated session once a user has entered their credentials. This type of attack is used to monitor activity and is usually carried out by local malware on the user’s endpoint or as part of a man-in-the-middle attack.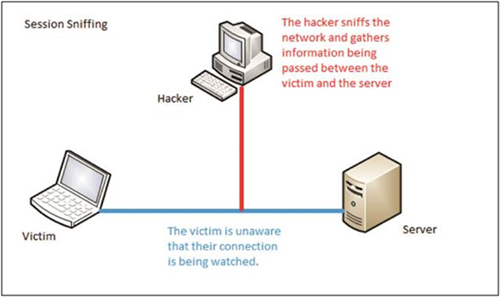
- DNS Based Phishing (Pharming)
DNS Based Phishing generally includes any technique that interferes with the integrity of a domain name search. As per Infoblox and DarkReading.com -The DNS threat index jumped almost 60% in 2015 as attackers became far more sophisticated in their campaigns.
Also, a new generation of inexpensive and quick startup domain names has made it easier for bad guys to set up shop in the DNS infrastructure. One example includes a phisher polluting the user’s DNS cache with information is used to redirect the user to a false, corrupted location.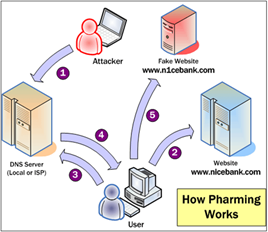
- Host File Poisoning
Hackers use this form of local pharming or DNS poisoning to corrupt the user’s host file. When a user enters a web address, it must first be converted to IP address using the hostname lookup before undertaking the DNS lookup. By “poisoning” the user’s host file, users are sent to websites impersonating others to steal information.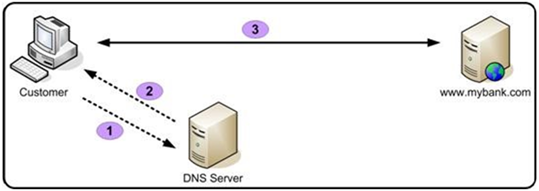
How to prevent Phishing
Phishers are trying to devise new Phishing tactics. The above list is in no way complete; however, you can do a bunch of things as a countermeasure to phishing threats.
- Anti-Malware: Adopt popular anti-virus/anti-malware solutions
- Web Filters: Determining what websites users can access using a risk-based approach
- Data Loss Prevention(DLP): Protecting data in transit, at rest, and in use
- Anti-Phishing Software: Containerization solutions for downloads from malicious emails and websites
- Using HTTPS for Transactions: Checking the padlock icon to ensure a secure transaction
- Spam Filters: Many email clients can detect potential spam (many being phishing attacks) and separate those emails
- Patch Management: Ensure system patches are up-to-date to mitigate many vulnerabilities targeted by phishing campaigns
Phishing is social engineering for a reason – because the attack vector relies on human interaction and involves tricking people into breaking standard security procedures. The best defense against Phishing is to impart security training and awareness to employees.
Why Phishing Fall and Fail Rates matter?
A typical phishing attack lures the target to read an email, visit a website, and reveal information. The common misconception is that the attack is successful only if the target reveals the information. However, this is not true.
An attacker essentially looks for information to plan the next move, which he/she can get based on user actions, even when there are no significant revelations of private data.
For instance, just by visiting the malicious website, the target can reveal information. Hackers can use this information for fingerprinting and understanding the kind of information that can attract a target.
The Fall Rate is the percentage of users (targets) who “fall” for the attack and visited that fake website.
The Fail Rate is the percentage of users (targets) who “fail” in the attack, visit the fake website, and reveal sensitive information
All employees who “fall” need not necessarily “fail,” which means that either they realized it was an attack (most likely the case) or didn’t proceed further due to other priorities. The gap means there is an excellent opportunity to train employees and make them aware of phishing tactics.
Educating employees with examples of good and bad behavior based on their actions and retaining that knowledge would be far more excellent than possessing knowledge gathered from generic training.
Aujas offers Phishnix, an automated spear Phishing diagnostic platform to analyze employee behavior to understand their reactions towards the simulated attack. The data from these simulations is leveraged to create awareness and training programs for employees and educate them on responding to a phishing attack.
To know more, visit the Phishnix page, or write to us at contact@aujas.com.





