Organizations are rapidly proliferating digitization initiatives at scale and speed. Though such initiatives are boosting revenues, expanding service offerings, and reducing costs, it is also forcing business leaders to reimagine their security approach to secure these broadened digital surfaces. This paradigm shift to digital capabilities has opened up greater risks to security breaches. Moreover, complex attacks are organized by professional cybercrime syndicates highly competent to launch decisive attacks with clinical precision.
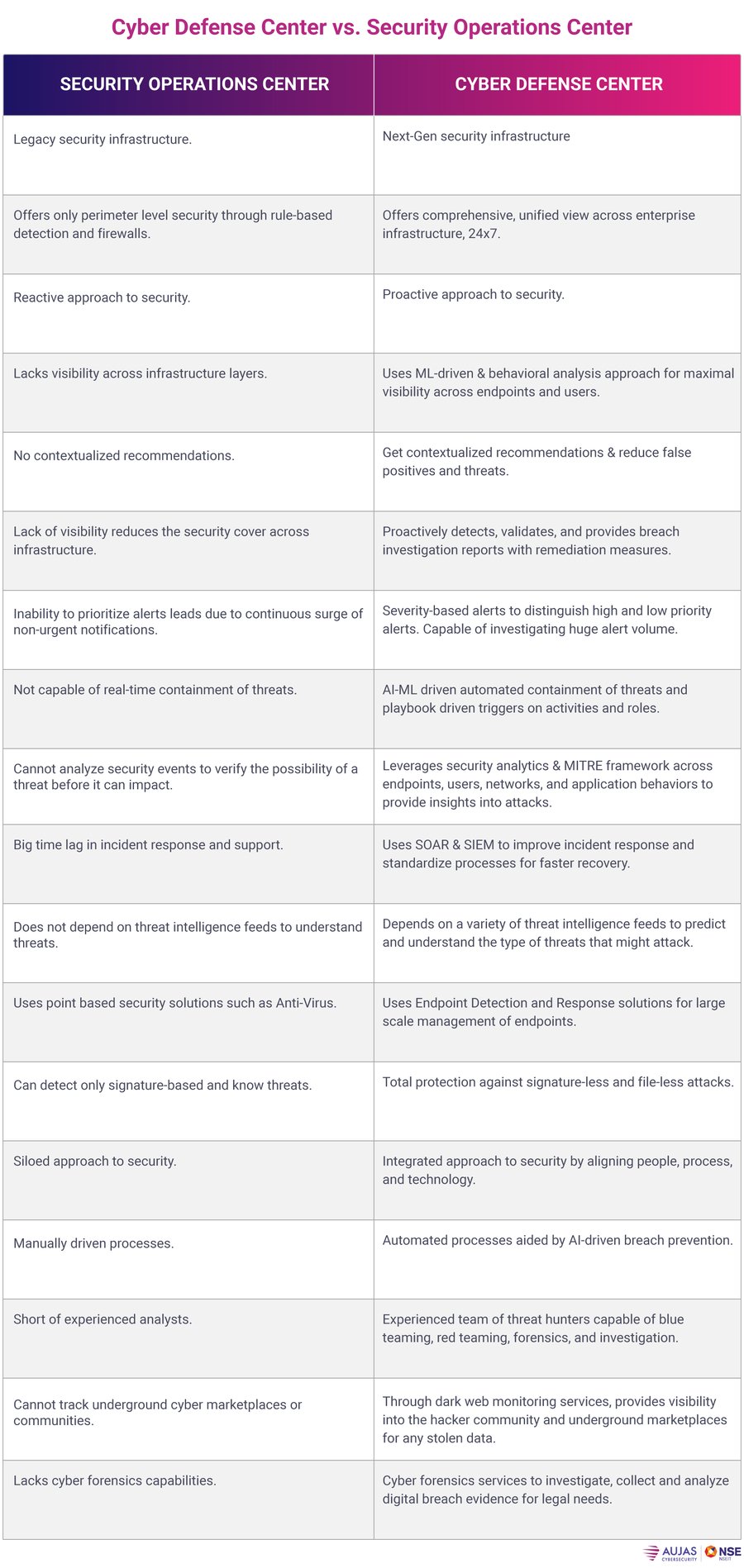
Limitations of SOC
A security operations center (SOC) isn’t enough to combat such power packed threats. Most of them are focused on network surveillance, monitoring, and alert triage, identifying indicators of compromise, and meeting SLA metrics. They lack the comprehensive visibility to endpoints, network traffic, Transport Security Layer (TLS) sessions, and encrypted network communication between servers and systems. This also prevents them from discovering zero day exploits.
SOC face process latencies and isn’t quick enough to meet the changes in system environments. The lag is also due to the lack of analyst understanding of the processes. Most processes are makeshift in nature and are not comprehensive due to staff shortage to improvize them, resulting in sluggish incident responses.
Technology is another bottleneck. It lacks next-gen tools to monitor and detect threats in containerized cloud applications critical for digital business. SOCs do not have analytics, threat intelligence, and alert filtering capabilities. This inability makes it challenging to clear large volumes of duplicate and correlated alerts to minimize alert fatigue and enhance threat detection. SOC cannot detect lateral movement of an attack due to lack of endpoint visibility. An EDR solution can overcome this dysfunction.
A SOC’s increased dependence on manual processes results in human errors. Security analysts respond to incidents based on their limited knowledge and experience, which results in slow, error-prone responses. These gaps can only be fixed through automation and integrating security systems working in silos.
SOC is more reactive in nature and depends on the analyst’s ability to respond to threats, causing delays in incident response. SOCs also have to be manually configured, patched, and protected to keep them operable. More often, SOC teams lack clarity on the environments they are trying to secure. This lack of information makes the infrastructure more vulnerable. Feeds on emerging threats and actionable Indicators Of Compromise (IOC) are essential for threat hunting, which, unfortunately, most SOCs are unable to execute due to a lack of resources.
Relying on SOC makes it immensely difficult to mitigate sophisticated threats. Transitioning from SOC to a cyber defense center is the only option.
Cyber Defense Center can replace SOC
The reactive approach of SOC can thrawt one-dimensional attacks but not multivector threats. Cyber Defense Center (CDC) is fully capable of taking on sophisticated, targetted, and dynamic multivector attacks such as ransomware and malware.
CDC can transform cyber defenses by proactively identifying threats-24x7x365. CDC rapidly initiates threat detection and response during an attack using endpoint detection tools, User and Entity Behavior Analytics (UEBA), rule-based detection, packet capture modules, etc., to quickly recover compromised devices and assets to mitigate the occurrence of further breaches.
It offers a holistic approach to security by synergizing prevention, detection, and remediation capabilities to offer 360-degree comprehensive visibility in a changing cyber environment. Powered by Azure Sentinel, a cloud-native SIEM solution with intelligent security analytics, the CDC provides sophisticated threat hunting and investigation capabilities to reduce mean time to recover and meet security demands at scale.
You can consider it the next-gen SOC required to secure the exponential increase of digital ecosystems consisting of IoT, social media, Big Data, cloud, and connected mobile devices. CDC is enabled by threat intelligence feeds, which provide actionable risk scores to make informed, real-time decisions. The analysis of these feeds offers valuable insights into adversary motives and capabilities. This helps you to predict, prepare and mitigate any risks associate with these attacks. By integrating the power of Managed Detection and Response (MDR), SOC, intelligent analytics, and automation, Cyber Defense Center offers proactive, ML-driven threat detection, monitoring, and response capabilities across infrastructure layers.
The threat landscape is compounding, and the dangers of intelligent breaches are growing every day. To stay compliant and secure, you need centralized, continuous monitoring and interoperability, which only a cyber defense center can provide. The first-generation APT defense systems are a parse. It’s time to adopt the power of a cyber defense center to validate security posture, strengthen defenses, and sustain security preparedness.
The Cyber Defense Center is the perfect answer to mitigate complex threats. To know more about how to secure your enterprise, write to us at: contact@aujas.com





