Red teaming is in talks these days, but very few organizations are walking the talk. Some are too confident about their costly infrastructure; some think that it is the same as VAPT, and some do not care.
The questions remain the same:
- Are we safe from hackers?
- Do we have adequate configurations in place?
- Are we doing enough due diligence to protect the business?
Here is an ideal use case scenario on how to initiate a red team assessment to test cyber defenses. The assessment focuses more on the approach and coverage using the MITRE framework. The framework advantages included scoping and tailoring TTP for progress tracking, clarity on project phases, and the goals which should be achieved.
Here are the benefits of using the framework vis-à-vis the disadvantages:
MITRE Approach
Two matrices by MITRE offer a simplified approach to the overall activity. The first matrix is related to passive and active enumeration, and the second about active exploitation. We will be calling this Phase 1 or PRE-ATT&CK and Phase 2 or ATT&CK, respectively. Comparing Phase 1 to reconnaissance would suffice. However, there is much more in the PRE-ATT&CK phase than just recon when looked at it from an adversary standpoint.
Phase 1 - PRE ATT&CK Phase
This phase has three sub-phases:
- Target Identification: The organization can be chosen depending on the sector, interest, and goal.
- Information Gathering: This involves active and passive information gathering related to people, organization, and processes.
- Adversary OPSEC: Here, the adversary prepares itself by setting up C2, creating bots, fake accounts, and framing stealth breach techniques.
Phase 2: ATT&CK Phase
In this phase, multiple plans are devised based on the collected information. For this initiative, the red team can formulate two plans.
- Plan A: Gain initial foothold using web application vulnerabilities.
- Plan B: Social engineering by using phishing and vishing techniques; since this can be too easy, this can be considered as a backup plan.
We will see how to execute Plan A in action as we advance.
The Red Team Approach
The project can be initiated with a meeting to discuss the objectives and goals. The Red Team usually has two objectives. One is to assess the security of the targeted organization, and the other is to follow the framework and leverage the same techniques used by a real adversary. Create a Red Team and assign each one of respective tasks to kickstart the initiative. Regular informal meetings can be held to provide updates, distribute tasks, and track tasks, etc.
Phase 1: PRE ATT&CK
Conduct passive reconnaissance at various fronts to discover information like IP address ranges, web applications, email IDs, credentials (if any), physical locations, and anything that could be of help.
Adopt the usage of OSINT tools, shodan, scripts, spiderfoot, and social media to squeeze out the information from all possible places. The essence of this phase is to gather information, and once the data is collected, you can evaluate them to verify which of them can be of help and what can be kept for future use.
Shown below are the tactics and techniques that can get covered as a part of phase 1. This includes using spiderfoot to gather information, LinkedIn to collect employee data and emails, DNS recon usage, setting up empire C2, persona development, identification of 3rd party software, connect with targets of interest through social media platforms, etc.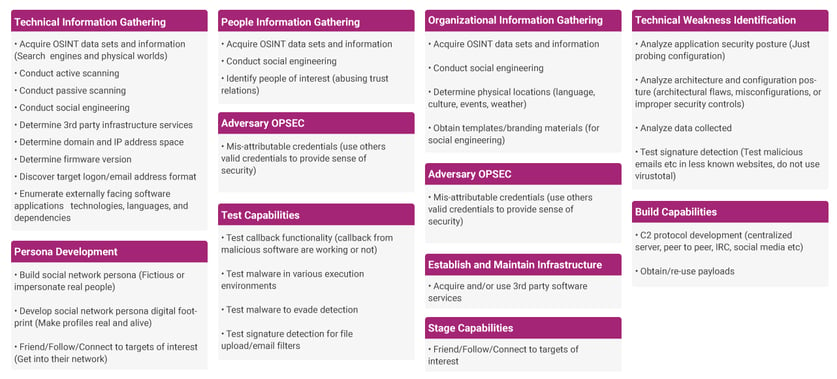
This phase can give the red team useful inputs to execute Plan A & Plan B:
- Information on web applications and IP addresses
- Improperly configured web applications - Plan A (Exploit)
- Personal information and contacts – Plan B (Social Engineering)
Phase 2: ATT&CK
Plan A: Identify a website used by the organization, this can be an AWS cloud-based application dashboard which can help you quickly get access to the directories.
By going through the directories, you can gain access to the file path to download the contents. Go through the content and grab the two AWS keys: SECRET_KEY and ACCESS_KEY. You can use these keys to connect and configure AWS in your system.
The data buckets are to be dumped, and you can move around like in a typical UNIX environment. Now, search the buckets for data. The files might reveal multiple LDAP service accounts and passwords used in the application.
If you know of the types of software in use, during the information gathering phase, check for Office 365 on the list. Gain access to the mailbox. Check whether Office 365 has Two Factor Authentication (2FA) enabled. Most of them don’t activate it and do not use their mobile numbers for registration. If they haven’t registered, use your mobile number to register and cover the persistence part.
If the user changes the password was changed, reset it using the second factor. Whenever a new registration is done for some application, they send a confirmation email on the mail ID. Using this information and searching through the emails, you can successfully register other applications along with the credentials.
From an application standpoint, you can move laterally from one application to another. You can also plan your last pass, and that can be the privilege escalation. In this case, the AWS penetration testing toolkit named PACU can be of help. You can generate AWS management console links by using the keys you have collected.
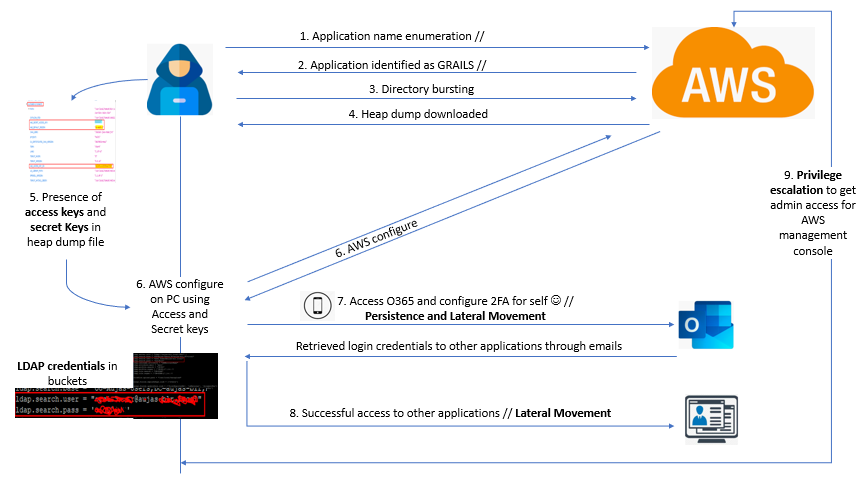
The management console will usually have the information related to the payments you have made, the services you have opted for, including confidential information.
You can cover a lot TTPs as a part of the attack phase. TTPs can be covered in a random order, not necessarily in one order. Use admin credentials identified in the publicly disclosed files to stop the billing cycle and create a direct impact rather than going through all the phases.
Phase 2 - Tactics and Techniques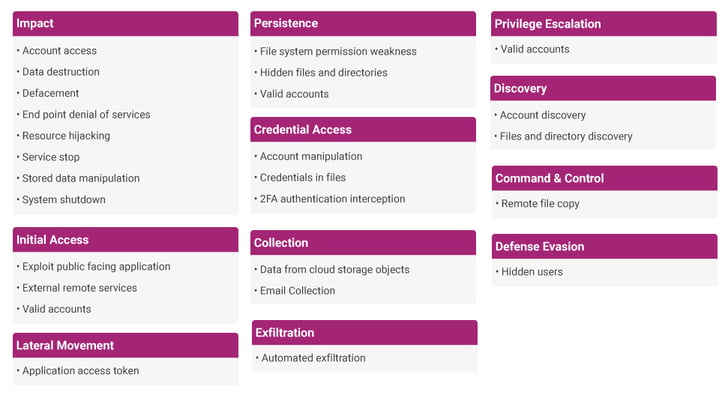
Timelines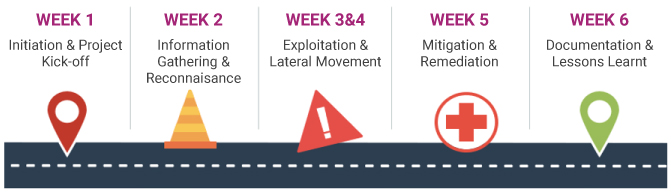
Conclusion
A proactive red team assessment is always fruitful. You can identify critical gaps in defense controls, which, if left unassessed, can lead to potential losses in terms of cost, reputation, and data. A Red Team assessment can help in the mitigation of severe security risks and up gradation of every organization’s security posture, reinforcing management, and client confidence.
The MITRE framework can be new to many security teams, from an execution point of view. From an enterprise security perspective, the security teams can leverage the MITRE framework to evaluate current gaps in defense controls, SOC capabilities, to improve the security maturity level of the organization
Key lessons from a six-week Red Team assessment includes:
- Be proactive in strengthening security posture.
- We are never secure. There is always a risk. Reduce it to an acceptable level.
- Effective security due diligence is needed to produce tangible value.
Now the question remains, are we safe from hackers? No, hackers will always be there, and so will be threats & vulnerabilities. Changing environments and new upgrades can give rise to new vulnerabilities. Security assessments must be continuous and periodic because hackers need 1% luck, whereas you required 100% protection.
Keen to know more about Red Team assessments and how it can help you discover cloud security risks? Mail us at contact@aujas.com.





