The pervasive use of cloud computing has increasingly become an integral part of every enterprise strategy. Cloud has brought in flexibility enabling enterprises to manage and scale IT resources to support changing needs quickly. An essential component of digital transformation, the cloud offers immense opportunities for value creation. Though digitalization has played a critical role in solving many business challenges, the actual value of this disruption will not accrue if the cloud security risks are not addressed. The collective value of digitization cannot be overstated; given the pivotal role it is playing across industry sectors.
The manufacturing sector is using autonomous robots to run process control systems. AR/VR wearables are also used to reduce any onsite accidents. Large shipping corporations are using digital twin technologies to build ships. Healthcare is leveraging robots in surgery, doctors are using connected devices for remote monitoring, healthcare guidance, and mobility. The automotive sector uses predictive analysis for autonomous vehicles, including RFID sensors for consumer applications and vehicle transportation and IoT devices to streamline operations. Banking is getting transformed through neo banking, resulting in branchless banking through digital platforms with open APIs. Banks are adopting Blockchain to enable international remittances by removing any intermediaries. E-Governance initiatives are driving digital identity programs to connect devices & people, enable new services and provide better citizen experiences. Oil and Gas segment is widely using predictive analysis, intelligent automation with OT/IoT platforms, and intelligent devices to run routine tasks such as on-field and support functions. Retail is embracing intelligent devices and IoT in a big way to improve customer experience and improve store operations. And lastly, the advent of 5G in telecom has accelerated the growth of APIs to support intelligent solutions such as IoT, unified communications, and edge computing.
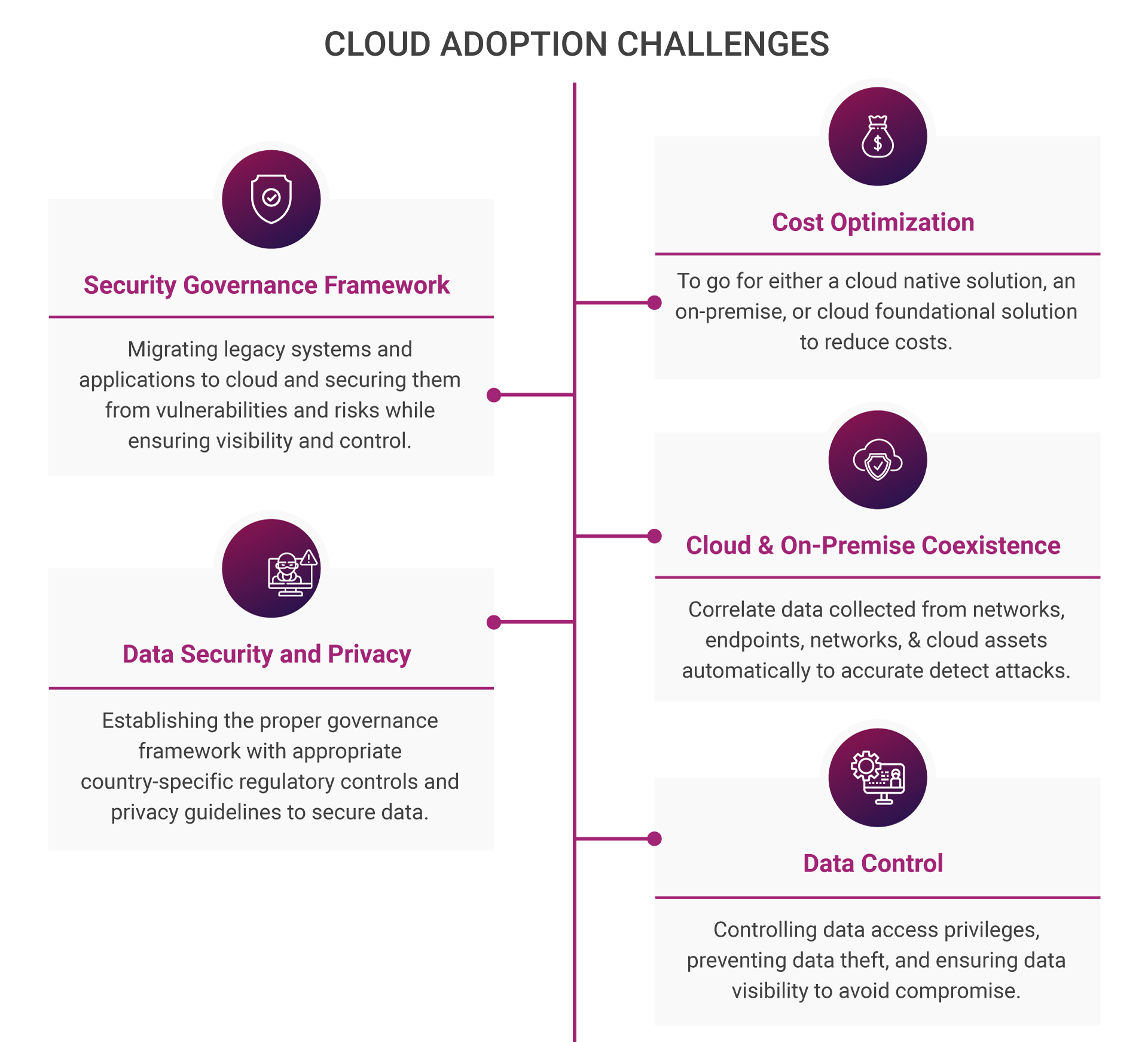
Cloud is everywhere with its set of challenges
As we have seen, every sector is going digital to stay relevant and productive. A key driver of this change is the cloud, and it’s everywhere in a digitized world. Although known for operational performance and agility, delivery models such as Platform as a Service and Infrastructure as a Service make the cloud a strategic part of the overall computing infrastructure. Every software driven service is getting migrated to cloud for supporting businesses and open new streams of revenue. Moreover, cloud enables better IT resources agility, scalability, operational performance, and security.
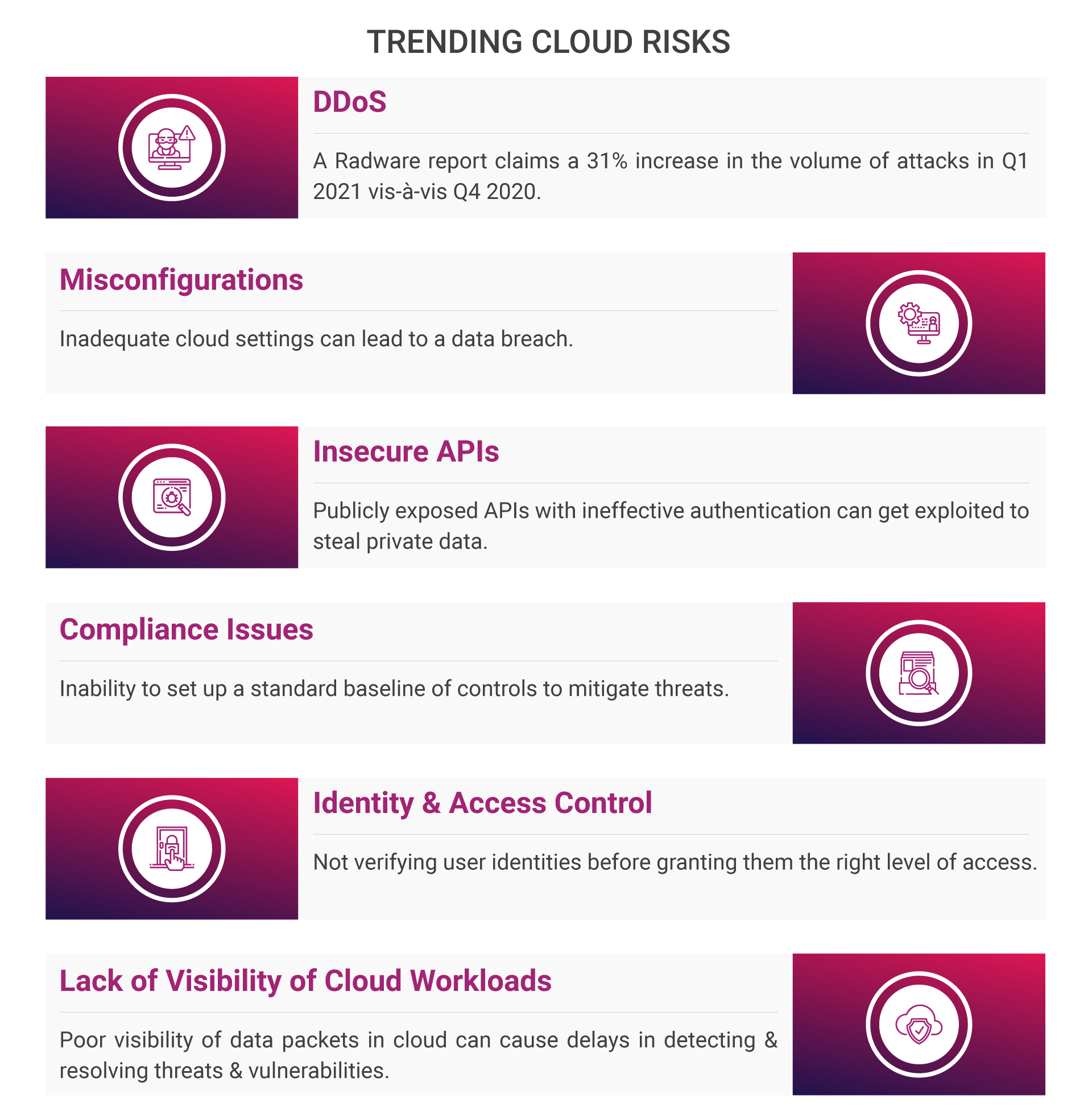
Key Cloud Risks
Protecting the cloud isn’t an easy task. Along with its advantages, it has security threat concerns. Based on recent attack trends, the risks can be of five categories:
Cloud security technology trends to fix these challenges
The cloud security challenges, as we see, are critical. A cloud ecosystem must be insulated from the dangers of the evolving cyber landscape. While making the shift to cloud, a business must focus on a better security approach to avoid oversight. With new threats emerging each day, the challenges must be fixed, as early as possible. Here are few cloud security technologies which are fast replacing older ones.
| Existing security technologies | Cloud security trends | |
| 1 | On-premises SIEM Monitoring | Cloud native SIEM platform |
| Expensive, resource intensive, steep learning curve, longer time to derive ROI | AI-ML automation to ensure cost savings, compliance, performance, and scalability | |
| 2 | Endpoint Security | Cloud based XDR security |
| Secure entry points in end user devices (servers, laptops, desktops, mobile) |
Automated data correlation across cloud workloads, data, applications & endpoint devices | |
| 3 | Security Operations | AI driven intelligent automation |
| Manual processes to monitor, detect, investigate & respond to threats | Infrastructure as a Code (IAC) service to automate security infrastructure provisioning, Cloud RPA to automate security processes | |
| 4 | Periodic Compliance | Continuous Compliance |
| Reactive approach to audit requests | Proactively monitor for compliance & regular risk assessment & be prepared for audit | |
| 5 | Identity Management | Cloud based Identity Management |
| High on maintenance, resource intensive, prone to security risks | Better security through multifactor authentication, password policies, & single sign-on, low maintenance, secured access control |
Irrefutable reasons to use cloud security solutions
Cloud security stacks can offer enterprise grade cloud workload protection, centralized visibility, zero-trust security controls, IAM authentication, enhanced data protection AI-ML driven automation and threat intelligence to detect and remediate complex threats in real-time.
 One significant advantage of a cloud security solution is the ease in pricing based on the per GB ingestion capacity. It’s a pay-per-use model—the price decreases with an increase in ingestion. Computing and storage capacities can scale for log sources and to support large ingestions. You can experience lower costs (Eg. for 1000 commissions per month) and hourly charges for any active use of machine learning models and services.
One significant advantage of a cloud security solution is the ease in pricing based on the per GB ingestion capacity. It’s a pay-per-use model—the price decreases with an increase in ingestion. Computing and storage capacities can scale for log sources and to support large ingestions. You can experience lower costs (Eg. for 1000 commissions per month) and hourly charges for any active use of machine learning models and services.
Cloud security strategies to ensure compliance
- Use of Native Controls
Cloud native security solutions must be adopted to bridge security gaps rising due to rapidly expanding digital landscapes. These solutions are intelligent and is driven by AI, threat intelligence, threat detection, and data analytics capabilities. It adopts an integrated approach and includes platform, infrastructure, and application security. Cloud native security controls offer next-gen threat prevention for every cloud asset and workload, enabling unified automated security to take on complex attack vectors. E.g., Azure Firewall, Azure Sentinel, Azure Security Center, AIP Key Vault, Microsoft Defender ATP, Azure Active Directory, and Azure Container Services.
- Employ Cloud Security Framework
Design and implement cloud security controls by leveraging Cloud Security Alliance’s Enterprise Architecture Diagram. Guided by methodologies and tools, it helps fulfill baseline security requirements that analysts can use to assess the operational readiness of cloud security controls. Use NIST cloud computing standards roadmap document to understand the standards, structure, and operations and develop the sector of actors, activities, and functions for use in developing cloud computing architectures. Leverage Microsoft Cybersecurity Reference Architecture to integrate Microsoft’s security solutions into existing security architectures and capabilities.
- Adopt Identity and Access Management
Enhance security for critical applications and ensure resource level access control by defining roles and grant permissions for users to access resources at different levels. Bring in Single Sign-On and Multifactor Authentication to secure data and apps and ensure remote workforce security and regulatory compliance. Cloud IAM has a single access control interface to improve visibility and monitoring across the ecosystem. Establish the Zero Trust Model to meet today’s security complexities of the mobile remote workforce, cloud migration and fix security gaps to reduce lateral movement of attack vectors.
- Establish Data Security
Improve data security with Azure Key Vault by encrypting keys stored in Hardware Security Modules (HSM) in a managed or shared environment. With Key Vault, there is no need to provision, configure, patch, or maintain HSMs. New vaults and keys can be quickly provisioned and centrally manage keys, secrets, and policies. There is total control of one’s keys as the applications never have any direct access to them. Key Vault can be scaled to meet peak demand without the need to deploy dedicated HSMs. It can also secure data in rest and transit.
- Maintain Continuous Compliance
Use Microsoft Compliance Manager to continuously monitor compliance across multi-cloud architectures (AWS, Azure, GCP) in day-to-day operations. Continuous compliance helps proactively heighten security readiness to threats and auditory requirements. Along with enabling ease and convenience, the compliance manager can take an inventory of data risks to manage the complexities of implementing controls and stay updated with the latest compliance guidelines. Prevent non-compliance by automating risk assessments, getting alerts on policy deviations, and enabling automated actions to implement changes in the cloud environment.
Cloud advantages are many. However, the risks related to cloud transformation must be considered, else there can be severe pitfalls. The cloud security approach is different from that of a non-cloud network. Large cloud deployments without next-gen security controls need a retrofit to address privacy and regulatory concerns. It’s time to choose a cloud security partner who can fully meet enterprise security objectives by understanding the enterprise threat profile and risk tolerance.
Aujas cloud security experts leverage market leading cloud security stacks to provide best-in-class protection at scale. To know more, talk to them at contact@aujas.com





