Author: Milan Singh Thakur
The trend of Smartphones has evolved drastically over the decade. The number of Smartphones in the market almost double up each year. The usage of mobile devices has increased the productivity and has changed the way organizations do business. This has led to the development of millions of Mobile Applications, but how many of these applications are safe? How many applications steal your personal data like your email, mobile number, location info, your Money?

Mobile applications are the most effective way used by attackers to spread malwares/rat onto devices. Many applications available on Google Play Store/Apple App Store are analyzed using automated analysis tools, which however, cannot detect sophisticated malwares like Zeus Bot or Dyre Wolf Banking Malware. Additionally, users install applications from unverified sources. It is highly recommended that all mobile applications undergo Security testing before being released on App Store or even to users.
Understanding How Mobile Malware works:
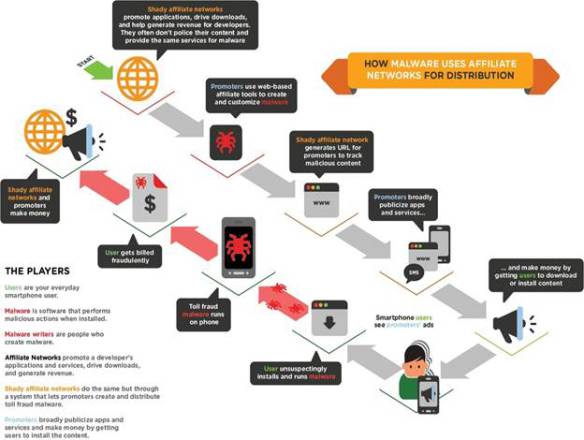
There are many free applications available on the internet, which has a backdoor that allows the attacker to gain access to our mobile devices. Moreover, users are prone towards downloading free software rather than buying it. This also includes patches, mod apks, and various cracked gaming applications. Given below is the actual depiction of how malware gets into our device:
Below given is the actual depiction of how malware gets into our device:
Most affecting and Active Malwares on Mobile Devices:
DangerousObject.Multi.Generic
Trojan-SMS.AndroidOS.OpFake.bo
AdWare.AndroidOS.Ganlet.a
Trojan-SMS.AndroidOS.FakeInst.a
RiskTool.AndroidOS.SMSreg.cw
Trojan-SMS.AndroidOS.Agent.u
Trojan-SMS.AndroidOS.OpFake.a
Trojan.AndroidOS.Plangton.a
Trojan.AndroidOS.MTK.a
AdWare.AndroidOS.Hamob.a
Android.Geinimi
SMS.AndroidOS.FakePlayer.c
Android.DroidDream AKA
Android.Rootcager AKA
AndroidOS_Lootoor.A
Android.BgServ AKA
Troj/Bgserv-A AKA
AndroidOS_BGSERV.A
Android.KungFu Variants
More are here:
AegisLab, Andr/Plankton-A, Andr/SMSRep-B/C, Android, Android Market, Android OS, Android.Adrd, Android.Adrd.A, Android.Adsms, Android.Basebridge, Android.Bgserv, Android.DroidDream, Android.Fokonge, Android.Geinimi, Android.GGTracker, Android.Gunfu, Android.Hippo, Android.HippoSMS, Android.HongTouTou, Android.Jsmshider, Android.LightDD, Android.Lovetrap, Android.NickiBot, Android.Nickispy, Android.Pjapps, Android.Rootcager, Android.Smssniffer, Android.Smstibook, Android.Snadapps, Android.Spacem, Android.Tonclank, Android.Trojan.SmsSpy.B/C, Android.Uxipp, Android.Walkinwat, Android.Zeahache, Android.Zsone, Android/DroidKungFu.A, Android/Sndapps.A, Android/YZHCSMS.A, AndroidOS_Adsms.A, AndroidOS_BGSERV.A, AndroidOS_Droisnake.A, AndroidOS_Lootoor.A, Botnet, F-Secure, Google, Lookout, Malware, Security, SMS, SMS.AndroidOS.FakePlayer.a, SMS.AndroidOS.FakePlayer.b, SMS.AndroidOS.FakePlayer.c, Spyware, Symantec, Trend Micro, Troj/Bgserv-A, Trojan-Spy.AndroidOS.Smser.a, Xuxian Jiang