Introduction
Venom, an acronym for “Virtual Environment Neglected Operations Manipulation”, is one of the “Virtual Machine (VM) Escape” category vulnerabilities in which an attacker may be able to break out of confined virtual machine and interact with the host operation system. However, VENOM is different from the rest of the VM escape vulnerabilities in a sense that it can be exploited even in the default configuration of the VM platforms and can spread to all other VMs running on the host.
This vulnerability resides in the floppy disk controller (FDC) driver code used in QEMU, a free and open source virtualization package used by many virtualization platforms like Xen, KVM, and VirtualBox. VMware, Microsoft Hyper-V, Linode, Amazon AWS and Bochs hypervisors are not impacted by this vulnerability.
The Vulnerability
As per the blog published by Jason Geffner, a security researcher from CrowdStrike who discovered this bug, the attack can be triggered by sending specially crafted data from guest virtual machine to Floppy Disk Controller (FDC) to cause the buffer overflow and ultimately execute arbitrary commands. This may result into (should be in) gaining control of the host machine and all other virtual machines running on the same host. Now, an attacker can access the sensitive data outside the exploited VM. In a cloud environment, it means gaining the access to other company’s (cross-tenant) data.
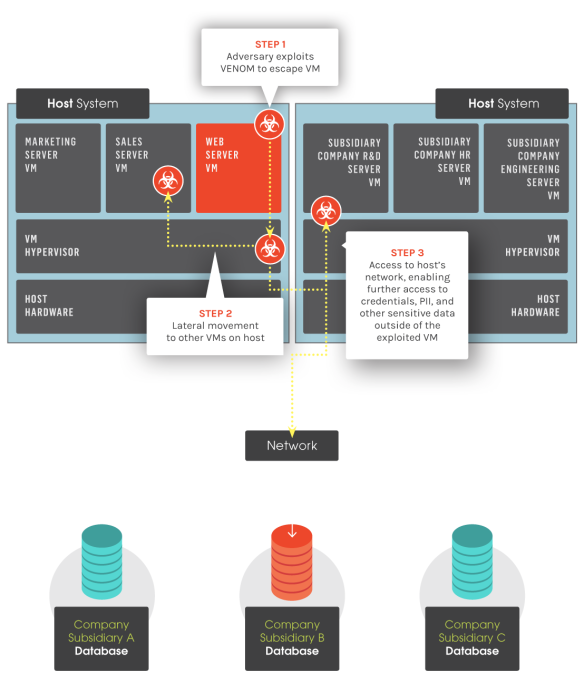
CrowdStrike has published the diagram that elucidates the attack flow -
Though this vulnerability seems to have a devastating impact, there are multiple factors we need to take into account while measuring the likelihood of this vulnerability getting wide spread –
- An attacker needs to be authenticated to one of the virtual machines in order to be able to exploit the vulnerability. Hence, it is not remotely exploitable vulnerability.
- CrowdStrike states that “Neither CrowdStrike nor our industry partners have seen this vulnerability exploited in the wild.” It means that exploit is not yet found or at least publicly not known.
- Even if the exploit is discovered, most likely this vulnerability will be used for targeted attacks and would not be used on large scale like Heartbleed.
Fixing the vulnerability
Even though there is no known exploit for this vulnerability, attackers may come up with the exploit as soon as the code is publicly available for them to reverse-engineer. Hence, it is advised to patch the vulnerability before attackers discover the exploit.
If you are running your guest system on any one of the affected virtualization platform, please contact your cloud service provider at the earliest. Patch information for different affected platforms is listed below –
QEMU
Patch information is published at http://git.qemu.org/?p=qemu.git;a=commitdiff;h=e907746266721f305d67bc0718795fedee2e824c
Xen
Patch information is published at http://xenbits.xen.org/xsa/advisory-133.html
All versions of Red Hat Enterprise Linux (RHEL) running QEMU:
Update system using the commands, "yum update" or "yum update qemu-kvm."
Oracle VirtualBox
Patch information is published at http://www.oracle.com/technetwork/topics/security/venom-cve-2015-3456-2542653.html
References
http://blog.crowdstrike.com/venom-vulnerability-community-patching-and-mitigation-update/
https://threatpost.com/oracle-patches-venom-vulnerability/112868
https://community.qualys.com/blogs/laws-of-vulnerabilities/2015/05/13/venom-hypervisor-vulnerability