The trend of Smartphone has evolved very drastically over the decade. The Smart devices almost double up each year. Through usage of mobile devices the productivity and the way organizations do business has rapidly evolved. This has given birth to development of millions of Mobile Applications, but how many of these applications are safe? How many applications steal your personal data like your email, mobile number, location info, your Money?

There are many ways to secure you mobile application and your data.
Efficient ways to ensure Mobile Security:
- Device trustworthiness
- Mobile Application Security
- Avoid Reverse Engineering of Apps
- MDM, MAM and MEM
- Strict SSL Pinning for Applications
- Encrypted Inter-device communication
Let us have a quick look into all the above mentioned ways to secure your mobile device. The understanding of these tips will ensure that your mobile device is not potentially vulnerable to attacks. However it is recommended to follow these tips throughout Mobile device life cycle.

Source: http://www.dameware.com/cmdprompt/byod-malware-threats-loom-high-in-2014.aspx
http://www.dameware.com/cmdprompt/byod-malware-threats-loom-high-in-2014.aspx
Device Trustworthiness: Most of the developers use common code for an application to support broad range of devices. This finally results in the application being exposed to a wide range of potential vulnerabilities across all the supported devices. Even though, Apple and Google provide regular updates for their respective mobile ecosystem, but it does not ensure 100% security. This gap invites attackers to exploit these loopholes, resulting in Jailbreak/Rooting of devices. Once jailbroken/rooted, attackers can easily run unverified applications or access the device using “root” capabilities. Therefore, it is necessary to question the Trustworthiness of the device.
Mobile Application Security: Mobile applications are the most effective way used by attackers to spread malwares/rat onto devices. Many applications available on Google Play Store/Apple App Store are analyzed using automated analysis tools, which cannot detect sophisticated malwares like Zeus Bot or Dyre Wolf Banking Malware. Additionally, users install applications from unverified sources. It is highly recommended that all mobile applications undergo Security testing before being released on App Store or even to users. Below given figure depicts how a compromised device breaches corporate security: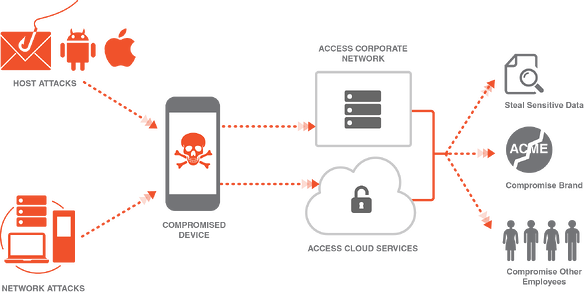
Diving into How Mobile Malware works:
There are many free applications available on internet, which contain a backdoor and allows attacker to gain access to our mobile devices. Moreover, users are prone towards downloading free software rather than buying it. This also includes patches, mod apks, and various cracked gaming applications.
Below given is the actual depiction of how malware gets into our device:
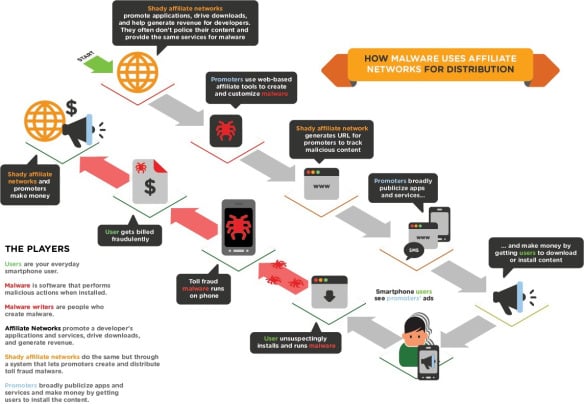
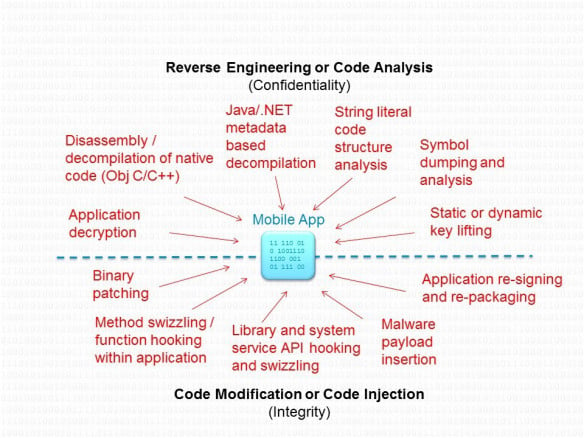
Avoid Reverse Engineering: Most developers do not follow the technique of Code Obfuscation. This leaves the app vulnerable to reverse engineering. Attackers can easily reverse engineer Android, IOS, Windows and Blackberry Mobile apps using freely available tools. If the code is not obfuscated, attackers can have a deep-dive into business logic used. Moreover attackers prefer to add malicious code in it, repack the application APK/IPA/COD/XAP and upload it to various sites from where it can be freely distributed to users. Source code piracy is one of the major concerns in today’s era. Reverse engineering compromises both confidentiality and integrity of the application/business. This not only causes loss of data, but causes defamation to the organizations.
MDM-MAM-MEM: Mobile Device Management (MDM) is like adding an extra layer of security and ensuring a way to monitor device related activities. MDM provides device platform specific features like device encryption, platform specific policies, SD Card encryption. Geo-location tracking, connectivity profiles (VPN, Wi-Fi, Bluetooth) and plenty other features are part of MDM Suite.
Mobile Application Management (MAM) is done by application wrapping i.e. injection arbitrary encryption code in the mobile application source. This is necessary for commercial applications or applications being developed in-house for Enterprise use. Additionally, white-listing/black-listing of application can be done. Features like Application Catalogue allow admin to push applications remotely to the devices for instant install, push remote updates and also remote removal of apps.
Mobile Email Management (MEM) ensures your corporate emails are containerized using advanced proprietary/free encryption algorithms. MEM ensures all emails remain inside the secure container, so that attackers get encrypted data even if they try to compromise the device data using USB cable on a system. Heavy restrictions on clipboard, attachments and trusted domains can be enforced. Nothing can move in-out of the secure container as clipboard is disabled. Even the attachments are downloaded and saved inside the secure container. To view the attachments there is secure document reader as well as secure document editor available in MDM solutions. Adding trusted domains will ensure that data from corporate email is not leaked to malicious/suspicious domains.

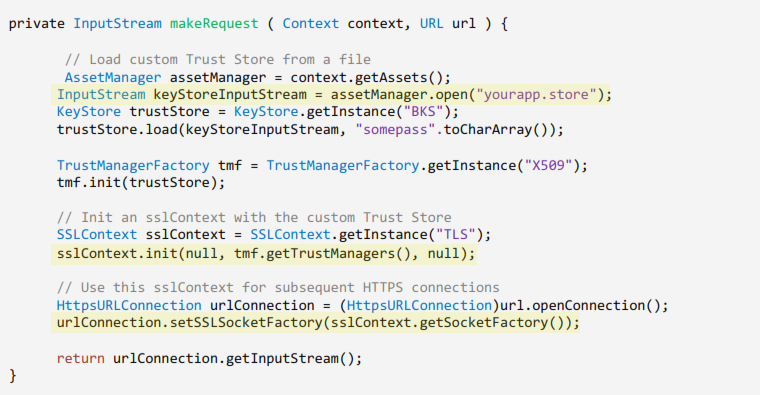
SSL Strict Pinning: What is SSL pinning? Why do we need SSL pinning in mobile applications? How to do it?
SSL pinning means hard-coding the certificate known to be used by the server in the mobile application. The app can then ignore the device’s trust store and rely on its own, and allow only SSL connections to hosts signed with certificates stored inside the application. This also gives a possibility of trusting a host with a self-signed certificate without the need to install additional certificates on the device.
SSL Pinning on Android: Simplest Way
PROS of Certificate Pinning:
- Increased security - with pinned SSL certificates, the app is independent of the device’s trust store. Compromising the hard coded trust store in the app is not so easy - the app would need to be decompiled, changed and then recompiled again - and it can’t be signed using the same Android keystore that the original developer of the app used.
- Reduced costs - SSL certificate pinning gives you the possibility to use a self-signed certificate that can be trusted. For example, you’re developing an app that uses your own API server. You can reduce the costs by using a self-signed certificate on your server (and pinning that certificate in your app) instead of paying for a certificate. Although a bit convoluted, this way, you've actually improved security and saved yourself some money.
CONS of Certificate Pinning:
- Less flexibility - when you do SSL certificate pinning, changing the SSL certificate is not that easy. For every SSL certificate change, you have to make an update to the app, push it to Google Play and hope the users will install it.
Check implementation details here:
https://www.owasp.org/index.php/Certificate_and_Public_Key_Pinning
Encrypted Inter-device Communication:
As the dependency on smart devices is heavily increasing, we need to watch out for our data being stolen in new ways. This clearly means there are multiple ways in which our personal and confidential data is being leaked out from our mobiles, tablets, smart watches and all other smart devices around us. Inter-device communication used in Internet of Things (IoT) is primary concern for penetration testers and the demand for smart device is increasing significantly. Below given image speaks it all:
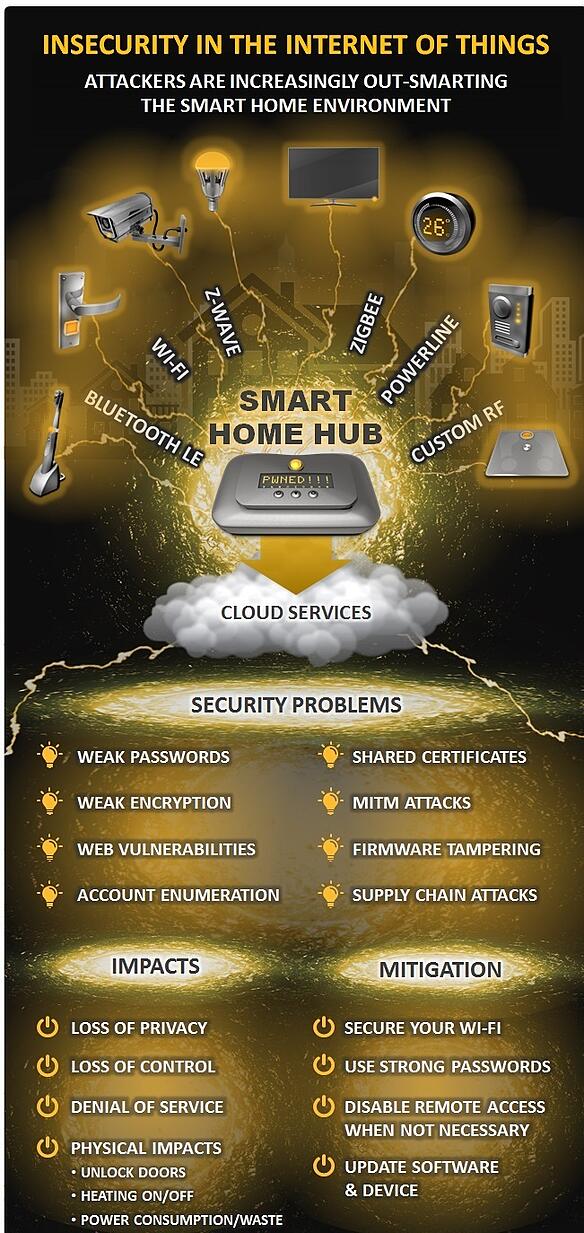
Image Source: http://www.symantec.com/index.jsp





