Introduction
TLS and its predecessor SSL are the security protocols designed to securely transmit the data between client and server to prevent eavesdropping and tampering. And the strength of these protocols is in the encryption keys used for communication.
In 1990s, NSA, the U.S. intelligence agency forced companies not to use strong encryption ciphers for SSL clients outside the U.S., so that they would be able to monitor the foreign traffic. This means, for RSA encryption, the maximum allowed key length is limited to 512 bits. It was an effort to align with the United States’ strategy to protect its own encryption technology and decrypt other countries’ communication. These low grade ciphers marked as exportable by the U.S. government are known as “EXPORT”.
This stringent export restriction was gradually eased by the U.S. government; however, the EXPORT ciphersuites were still supported by some of the SSL servers and clients. Almost after a decade, this resulted into the realization of a vulnerability named as “FREAK” (Factoring Attack on RSA-EXPORT Keys).
The vulnerability
During SSL handshake phase, SSL client and server agree upon the ciphersuite to be used for encrypted communication. A cryptography bug in SSL clients like OpenSSL forces them to accept a weak RSA-EXPORT cipher during the “cipher negotiation” phase between the SSL server and client, even if they did not ask the server.
In a standard TLS handshake process (as depicted in the flow diagram below), the client and server exchange random numbers and a Pre-Master Secret. Client and server then combine these numbers and pre-master secret with additional data to create their secret key, called the “Master Secret”, which is then used by the client and server to generate the session key used for encryption.
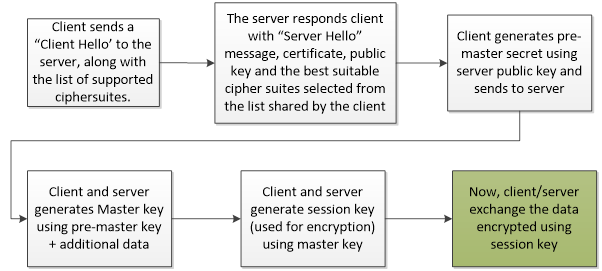
The FREAK vulnerability can be exploited by the attacker (Man-in-the-Middle) as shown in the flow diagram below:
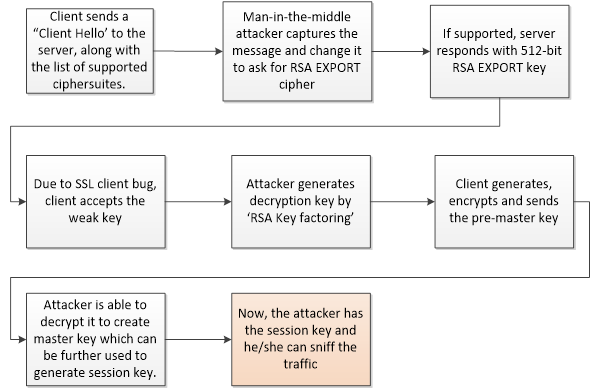
This vulnerability can only be exploited if the SSL client is vulnerable to the bug and server supports EXPORT keys.
Who are affected?
This vulnerability affects both server and client.
Servers:
All servers that support EXPORT keys are vulnerable to FREAK attack. You can test if your website is vulnerable here.
Currently, a large number of websites are affected by this vulnerability. The website freakattack.com publishes the current list of affected popular sites. Also, the list of Top 1 million affected domains is available here
Clients:
Most of the well-known browsers have started patching the vulnerable versions and this vulnerability soon may become obsolete for browsers. You may test if your browser is vulnerable by visiting website, FREAK Browser Test
Some of the TLS clients including OpenSSL, Apple's SecureTransport and Microsoft’s SChannel have this bug.
Vulnerable TLS client libraries include
• OpenSSL (CVE-2015-0204): versions before 1.0.1k.
• BoringSSL: versions before Nov 10, 2014.
• LibReSSL: versions before 2.1.2
• Mono: versions before 3.12.1 are vulnerable.
A fix is being test for following libraries:
• Apple’s SecureTransport
• Microsoft’s SChannel
• IBM JSSE
Fixing the vulnerability
Server side:
Disable the support for RSA EXPORT keys.
Client side:
Update the browser to the latest version as soon as it is patched and make sure that all relevant TLS libraries are updated.
References:
http://blog.cryptographyengineering.com/2015/03/attack-of-week-freak-or-factoring-nsa.html
https://freakattack.com/
https://www.smacktls.com/




