As new technologies are coming up day by day, we tend to ignore the older ones. Taking advantage of this, attackers always try to make you a victim by getting access to the older technologies. Modem is one of these old age technologies, so beware!
War dialing is one of the oldest techniques to find out the telephone numbers, from a given number range that are directly connected to internet. Or you can say it is the most common technique for getting unauthorized access after implementing firewall and other intrusion detection system. War-dialing work like a backdoor access. It can not only provide access to the computers but provide access to the whole network. Although it’s a very old attack but still possible. It’s illegal to perform war-dialing without organizations approval (figure 1).
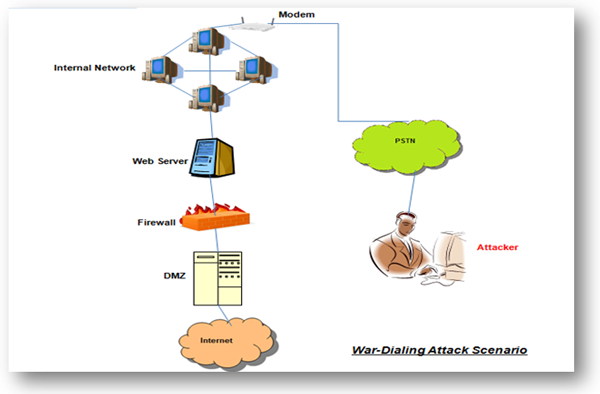
Figure1: How an attacker compromise network using war-dialing
Why War-Dialing Exercise is useful for Organization:
During war-dialing we look for the modem which is connected to a telephone line. The modem may be connected with router, desktop machines, Voice Mail Box, Control Programs, PBX etc. Any compromise of these can cause loss of reputation as well as data loss to the organization. Organizations used these dial in modems to facilitate employees who wanted to work from home or those who were traveling. For remote access different software like pcAnywhere etc. were used. There is a high chance that a version of this software may still reside on the server and have authorization issue or any authentication by-pass issue which may lead to unauthenticated access that in turn can compromise the network.
Apart from this, an employee may install a modem for accessing his personal use like naukri.com, personal emails and accessing his computer from home etc. and will always try to keep it hidden from the organization. It is also possible that unknowingly a user configured the modem without security password and a smallest mistake like this can lead to compromising the network.
War-dialing exercise helps to analyze:
- Identify Modem, fax, voice mail box etc that currently present in organizations.
- Identify insecure system.
- Identify modems that are not securely configured.
- Identify insecure dial in accounts.
Practical Scenario:
In one of our projects, client wanted to identify any available insecure modem installed in the organizations network. We were asked to perform a war-dialing exercise over the entire phone network. As this was a planned exercise and there was a fair chance that there could be employees who used modem during working hour and stopped after working hour or vice-a-versa. So it was essential for us to perform war-dialing during office hours as well as non office hours.
Approach we follow:
We prepared a list of numbers that we would dial and accordingly divided the entire list into several lists as per our project duration plan, so that we could perform this exercise in a smooth way. The list was fed in the war dialer tool and run. The result was analyzed and we found a few modems which that were asking for username and password. As we were not familiar with the account lockout policy we used some common usernames and passwords like admin-admin. But we failed to login and in one system we observed that remote access software was being used. When checked for specific vulnerability, we found some authorization issues that we tried to exploit and succeeded.
Apart from this, on the remote access software installed when we clicked on “allow anyone” it led to unauthorized access.
Steps for War-Dialing:
War dialing exercise starts with the following phase:
- Getting Approval from Organization.
- Information Gathering: Finding telephone numbers, this can be done with the help of various sites (for attackers) like whois.sc, their websites contact us page, telephone directory etc.
- Listing all the numbers as per our exercise time plan.
- Perform Scanning with the help of tool like THC-Scan, Toneloc, phonesweep etc.
- Analyzing result.
- Reporting.
Available War-Dialing Tools:
- THC-Scan (Freeware & Best open source war-dialer tool )
- ToneLoc (Freeware)
- Iwar (freeware)
- Modemscan (freeware)
- Phonesweep (Commercial)
- Telesweep (Commercial)
- Other tools: PhoneTag, Warvox, iwar etc.
Lab setup:
For setting a lab, one needs to have.
- Computer
- Telephone line
- Modem
- War-dialing software.
In this exercise we are using THC-Scan as the war-dialing software.
After Downloading THC-Scan, we will see a lot of documents including help. READ ME file that shows how the tool needs to be used. Further there is an executable file by name MOD-DET.EXE that detects available modem in computer and provides hardware information. Sometimes you get warning message that can be ignored. Once modem is detected you get irq, base address and com number, that is used for configuring THC-Scan.
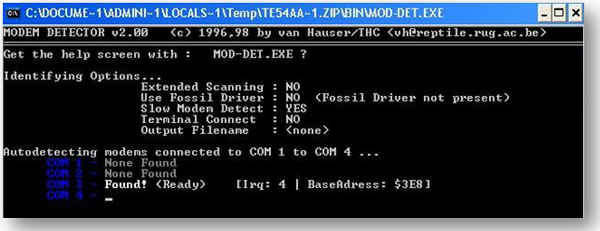
Figure2:- MOD-DET.EXE shows modem COM Port and other details
After finding modem port, base address and irq, launch TS-CFG.EXE. This executable file is used for configuring tools and other settings according to the scan strategy.
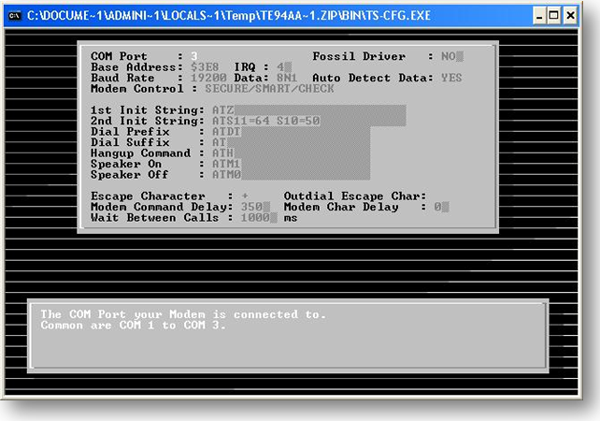
Figure3:- TS-CFG.EXE Configuration executable file
While launching TS-CFG.EXE, it is important to write the same COM Port and Base Address value which was earlier detected by MOD-DET.EXE, else it will not work. There are options available to dial the number in a sequential or random order. Timeout for calling numbers and various other settings are there that can be changed according to the testing approach. Once the configuration is finished THC-SCAN.EXE can be launched using the command thc-scan filename.dat /m:123-xxxx /r:1000-9999
The /m:, or mask, option specifies the prefix and range of the telephone numbers to be dialed, prefix are those numbers that are common to all numbers, while /r is range that will be marked as ‘x’.
Example: 111-1111 and 111-9999, we can mark it as 111-xxxx. The data is stored in the filename.dat.
In the above scenario we did not use 'filename.dat', because in case it is used .dat file will need to be deleted every time as it is created inside THC-Scan folder.
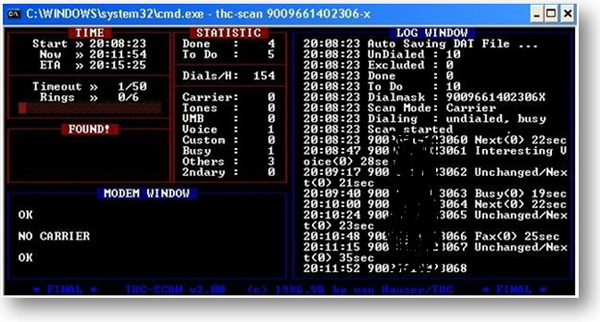
Figure4: War-Dialing Exercise using THC-Scan
In the above figure dialing number starts from 900XXX… here 9 is our ISD Dialing lock Code.Therefore, if any other organization does not use any ISD Lock code, they can simply dial the number using ‘00’ prefix. For example, if someone wants to dial any ISD number 123456789 then he/she can dial '00123456789'. THC-Scan will automatically detect the type of line but to speed up the process the user can press keystrokes depending on the device they want to opt for. For example if it is a modem they want then they can press “C”, for voice mail box press “V”, or for interesting voice press “I” etc.
Possible Problems which may come during War-Dialing Exercise:
First thing that comes to mind, is how to detect whether it is a modem or any other device, as there are a number of answering devices. Actually this classification of answering devices is done based on their unusual tones. For example fax tone is like a periodic tone. If you find any device connected or find any output of device which is not readable, then try to connect it with a terminal emulator and send some input e.g. help and then observe the response. Apart from this, try to increase your log size and connect with PPP connection and if remote device replies, then try to login via brute force or any guessing attack.
One can also try to dial the suspicious number internally (if possible) and observe the response. Apart from this there is a high chance of generating false negatives so cross verify the findings of the tool before reporting.
Understanding Output of THC-SCAN:
Few of the outputs are given below while performing War-dialing exercise
Busy: - These are the numbers which were busy during war-dialing scan.
Timeout: - If no response is received then number is marked as Timeout
FAX: - They have a different tone as compared to the ringing tone. War-dialing tool can easily detect fax tone.
Voice: - War-dialer software detects whether it’s human voice or system voice. As per the result it marks number as a VMB “Voice Mail Box”
Interesting: - If any unusual voice is detected it is marked as interesting.
Carrier: - These numbers that have end to end connectivity are marked as Carrier.
Now, what after finding rogue modem?
War-dialing tool generates a log file for all the numbers dialed. Look into the log, checks for modem device and then start penetrating it to find unauthorized access. Get access to the modem can be done in a number of ways:
- Try brute force i.e. using the username and password with the help of automated tools. To perform brute force large set of usernames and passwords are required, that can be easily found on Google. No doubt, it’s a time taking process.
- Use hyper terminal program, dial the modem, guess the username and password and get access, but the problem with this approach is that the number of dial in attempts is limited, after which it will hangs up.
- It is also possible to install backdoors, Trojans or key loggers which can easily capture username and password and helps us log in.
- Observe login screen banner, if any, and then try to search specific exploits of that vulnerability.
General Test on the modems:
- If it requires a user name and/or strong password to gain entry to the system.
- Auto answer is enabled on the modems or not.
- If there is Banner information from login screens.
- Brute force on login screen
- Can modem give access to Demilitarized Zone (DMZ) network.
- Can it create DDoS Attack
- User enumeration is there or not.
Conclusion and Recommendation for Modem Security:
Although War-dialing is an old school technology, it has its advantages.
- Do not use any Banner on login screen. This will prevent the attacker to from gaining any information which may lead to further attacks.
- Disable Auto Answer on modem.
- Use Call Back option to prevent unauthorized access.
- Enable Lockout policy.
- Enable logging.
- Use modem firewall.
- Use strong password.
- Prevent disclosure of phone numbers which have modem configured.
- Use modem in different range of phone number.
- Periodically change remote dial access number.
- Prepare remote access policy & modem security awareness training.
- Periodic Desk to desk check
- Educate all users on modem usage.
Prevention while using War-Dialing:
This activity must be done during off hours. So that one cannot answer the phone when we call that number, if they answer then the results change.
In THC-SCAN there is an option of dialing numbers in sequence. Depending on the policy, if you are dialing numbers sequentially then there is a fair chance that organization (if they don’t know, for hackers) may block your number and may create legal issues. So it is advisable to use random dialing for performing war-dialing exercise.
About Author: Nitin has been working with Aujas as a Security Researcher in the Telecom Security domain. With a rich back-ground in application, Mobile and net-work security, Nitin is now involved in researching about new and emerg-ing threats to the Telecom Core Nodes. Apart from Research, Nitin is also in-volved in assisting in the implemen-tation of security measures for Fixed/ Mobile Network (2g/3G/LTE) and core fixed network systems to regulate access to specific network elements for the secure oper-ation of the core fixed network and all its variants
Disclaimer: This article was published in Hakin9's December 2012 issue - http://hakin9.org/how-to-protect-your-company-against-intruder-with-hakin9-122012/


