Introduction to Azure
The Windows Azure Platform is a Microsoft cloud platform offering that enables customers to deploy applications and data into the cloud. Windows Azure Platform is classified as ‘platform-as-a-service’ and is part of Microsoft's cloud computing strategy. It provides developers with on-demand computing and storage space to host, scale and manages web applications on the Internet through Microsoft datacenters. The platform provides a cloud operating system called Windows Azure that serves as a runtime for the applications and provides a set of services that allows development, management and hosting of applications off-premises.
Windows Azure has three core components: Compute, Storage and Fabric. As the names suggest, Compute provides a computation environment with Web role and Worker role, while Storage focuses on providing scalable storage (Blobs, Tables, Queue, and Drives) for large-scale needs. Fabric makes up the physical underpinnings of the Windows Azure platform similar to the network of interconnected nodes of servers, high-speed connections, and switches.
Conceptually, the repetitive pattern of nodes and connections suggests a woven or fabric-like nature. Compute and Storage components are part of the Fabric. It also provides high-level application models for intelligently managing the complete application lifecycle, including deployment, health monitoring, upgrades, and de-activation.
Microsoft Azure Security
Cloud security is an evolving world with new threats and challenges. A smart customer would look at all the necessary security risks and would handle all data in cloud with clear risk mitigation plans. Security in the Azure platform is of paramount importance and Microsoft has built security controls into the platform.
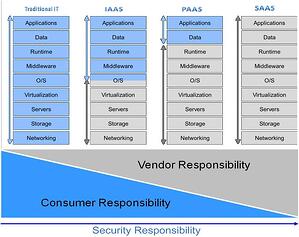
Cloud computing models and the security responsibility matrix are defined in the table at right.
Microsoft’s Azure Platform falls under the PAAS model. Microsoft has implemented and provided various security features such as:
- Identity and Access Management at all levels
- Isolation of data through separate physical containers
- Encryption of data in the fabric through on demand
- Run time security Full trust versus Partial trust
- Security libraries for security
Though Microsoft has built-in security in its architecture with App fabric and SMAPI (Service Management API), companies that move to this platform must ensure the security of their independent applications. The application developers have to use the right tools and APIs to secure and deploy the application.
There is no “Magic Wand for Security”
Azure has ensured security at various layers within its architecture and at various VM and its Fabric engine. This security will ensure the customers that data is not leaked outside of their VM. Though Azure has security innovations to aid application development and deployment, the responsibility of securing applications is left to customer.
This means if end-customers have to build applications that are secure by design and secure by default it is in the hands of the Azure application developers and architects. Security is not static and it’s a constant threat which has to be mitigated at all levels of the application and platform. Azure provides many security API’s that could be used to protect the data and access but it’s up to the end-customer to decide what is appropriate for the kind of data that needs protection.
As the chart above explains, the PAAS model requires security SME’s with core knowledge on the platform related security, with understanding of the Windows Azure runtime trust models and the security protections and responsibilities of each cloud layer. Companies need to build complex “Gatekeeper” based design with the help of design patterns such as control access context, advisor, interceptor, and web roles patterns.
The latest addition to the foundational technologies in the .Net framework is the Windows Identity Foundation (WIF). It enables Azure developers to offload the identity and authentication logic, providing a solid development mode based on separation of concerns pattern. A simple or traditional role-based access to advanced and sophisticated access control policies can be implemented with the help of WIF.
When it comes to cloud-based solutions, it is more important for software designers and developers to anticipate threats at design time than is the case with traditional boxed-product software deployed on servers in a corporate datacenter. Designing secure applications in Azure is about choosing the right sets and understanding the responsibilities. A traditional model of application development will result in the same vulnerable application. But with better knowledge on Azure platform, it’s possible to build more secure applications in less time and with less effort.
Developers and designers also need to understand the basics of building applications on cloud:
- Build cloud apps, not apps in the cloud
- Design fault tolerant systems, nothing fails
- Design for scalability
- Loosely couple application stacks (IOC)
- Design for dynamism
- Design distributed
- Build security into every component
- Backup application & user data
- Distribute applications
Conclusion
Computing solutions that use Windows Azure are very compelling to companies wishing to trim capital expenditures. However, security remains an important consideration. Security architects and developers need to understand the threats to the software developed for “the cloud” and use appropriate secure design and implementation practices to counter threats in the cloud environment.
The progression from classic client-server computing, to web-enabled applications, to applications hosted in the cloud, has changed the boundaries of applications and a striving need for compliance drives security. These boundary shifts and compliance requirements makes understanding the threats to Windows Azure-based software all the more important.